[ad_1]
Some malware starts life as a legit app until an update adds some malicious features
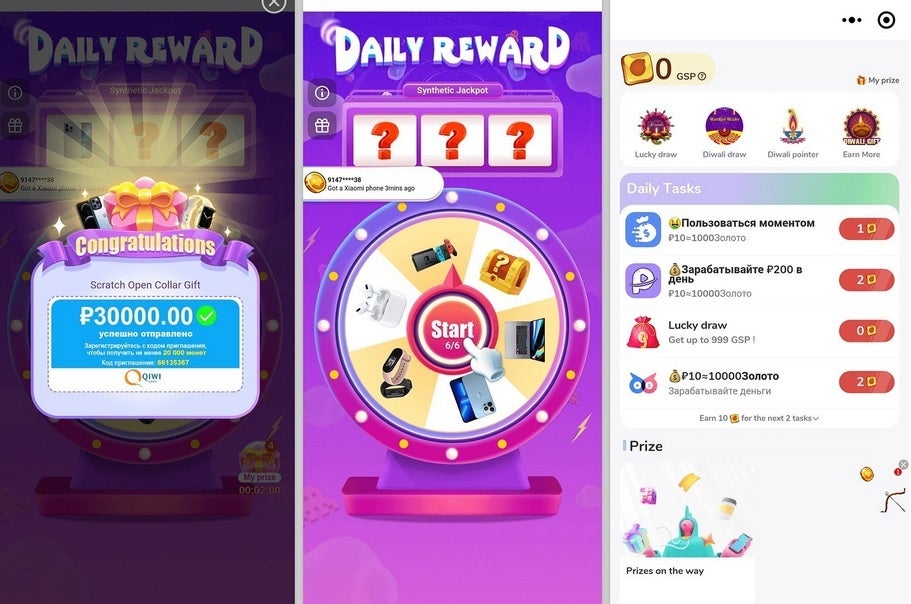
Mini-games like these contained malware and were installed 451 million times from the Google Play Store this year
By the time the iRecorder app was considered to be malware in May 2023, it had been downloaded 50,000 times. But the iRecorder story is illustrative of how these apps slip through Google’s checkpoints; they start life as a regular app that does only what the developer says it does. But after some time goes by, an update is sent out that includes malware, and instantly that benign app you installed on your Android phone has become dangerous.
35 million installs were tallied for clones of Minecraft which contained adware
Once these apps were opened on a phone, the malicious payload was downloaded on the device which would then open a browser window that the phone’s user could not see. The browser would direct itself to sites offering paid subscriptions and after intercepting confirmation codes, the malware would sign up the device owner for paid subscriptions through his/her cellular account which the app had been able to access.
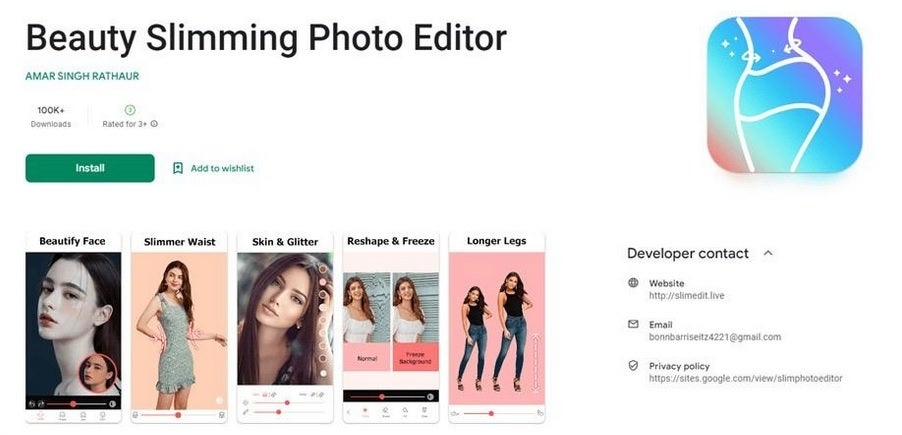
This app signed up users for expensive subscriptions without their knowledge
One of the most distributed malware apps that came from the Google Play Store last year were apps of Minecraft clones. Because of the popularity of the real Minecraft app, 35 million downloads were tallied under such names as Block Box Master Diamond. These apps contained adware called HiddenAds that ran ads in the background that the user could not see. While this made money for the bad actors, these apps would negatively impact the battery life of the phones on which they were installed.
One thing you can do to prevent yourself from installing malware is to check the comments section in the Play Store on each app from an unknown developer that you want to install. Forget the positive comments with high scores because those can be faked. Instead, check the negative comments with low ratings as these will probably be the ones that give you the true story behind the app.
Look for red flags in these comments from those who have installed the app on their phones. Such complaints include reduced battery life, overheating, and the constant freezing of a device. Also, check the app’s Play Store listing for spelling errors, and grammatical mistakes; if something doesn’t look right, your best bet is to refrain from installing the app.
[ad_2]
Source link
