[ad_1]
The 8220 Gang is exploiting multiple vulnerabilities, including the Oracle WebLogic Server vulnerability, to propagate cryptojacking malware in the Americas, Europe, and Africa.
Imperva Threat Research has discovered undocumented activity from a hacker group known as the 8220 gang. This group is known for mass malware deployment using an ever-evolving arsenal of TTPs. The 8220 gang mainly targets Windows and Linux web servers with cryptojacking malware.
The 8220 gang, believed to be of Chinese origins, was first identified in 2017 by Cisco Talos when it targeted Drupal, Hadoop YARN, and Apache Struts2 applications for propagating cryptojacking malware. the group exploited Confluence and Log4j vulnerabilities, and recently, Trend Micro found them leveraging Oracle WebLogic vulnerability (CVE-2017-3506) to infect systems.
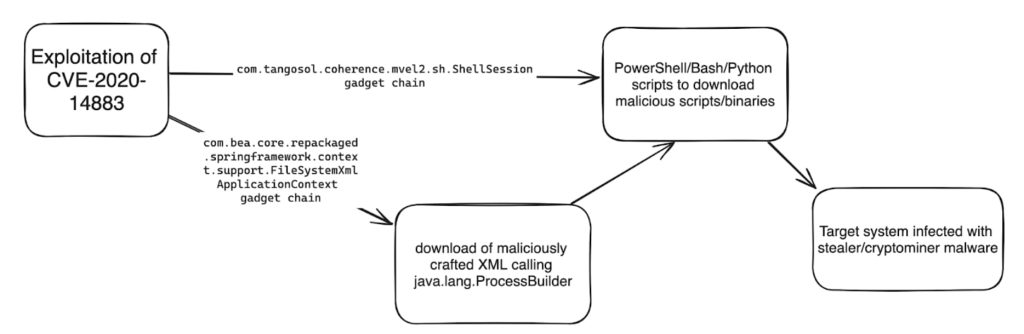
According to Imperva’s blog post, the 8220 gang is also exploiting CVE-2020-14883, a Remote Code Execution vulnerability in the Oracle WebLogic Server, to spread malware. This vulnerability allows remote attackers to execute code using a gadget chain. It is often chained with CVE-2020-14882 (authentication bypass vulnerability) or leaked/weak/stolen credentials. The gang uses two gadget chains; one loads an XML file, and the other executes commands on the OS.
Driven by financial motives, this gang uses simple exploits to target vulnerabilities and exploit easy targets. Despite their unsophisticated nature, they constantly evolve their tactics to evade detection. Attributing attacks to this group is straightforward due to their use of traceable IoCs and TTPs, frequently reusing the same IP addresses, web servers, payloads, and attack tools.
The 8220 gang uses various methods to target Linux hosts, including cURL, wget, lwp-download, python urllib, and a custom bash function. They also use a PowerShell WebClient command on Windows to execute a downloaded script.
In another variation, they use a gadget chain to run Java code without an externally hosted XML file. The injected Java code evaluates whether the OS is Windows or Linux and executes the appropriate command strings. The downloaded files are executed, infecting the exploited hosts with known AgentTesla, rhajk, and nasqa malware variants.
According to Imperva researchers, the 8220 gang appears to be an opportunistic group because of its target selection, which includes healthcare, telecommunications, and financial services.
It mainly targets organizations in the United States, South Africa, Spain, Columbia, and Mexico. Moreover, the gang prefers using custom tools written in Python in their attack campaigns, and the attacking IPs are associated with known hosting companies.
Imperva Cloud WAF and on-prem WAF have identified and mitigated web vulnerabilities used by the 8220 gang for malicious activities. These vulnerabilities include CVE-2017-3506, CVE-2019-2725, CVE-2020-14883, CVE-2021-26084, CVE-2021-44228, Apache Log4j JNDI, and CVE-2022-26134.
Imperva is urging organizations to maintain security. Enterprises should patch their applications and implement multiple security measures to protect against falling victim to such groups.
RELATED ARTICLE
- Patched OpenSSH Exploited for IoT, Linux Cryptomining
- Hackers mining Monero on Microsoft SQL databases for last 2 years
- Malicious Chrome extensions stealing data with cryptomining malware
- Cryptomining, Malware Flourish on Misconfigured Kubernetes Clusters
- New JaskaGO Malware Targets Mac and Windows for Crypto, Browser Data
[ad_2]
Source link