[ad_1]
Undetected for Over 11 Months, AsyncRAT Lurked on Systems of Sensitive US Agencies with Critical Infrastructures, reports the AT&T Alien Labs.
Cybersecurity researchers at AT&T Alien Labs have discovered a campaign delivering the old and notorious AsyncRAT, a remote access trojan, to targeted systems over 11 months. The open-sourced RAT, released in 2019, has been used in multiple campaigns by various threat actors, including the APT Earth Berberoka (or GamblingPuppet) due to its keylogging, exfiltration techniques, and initial access staging.
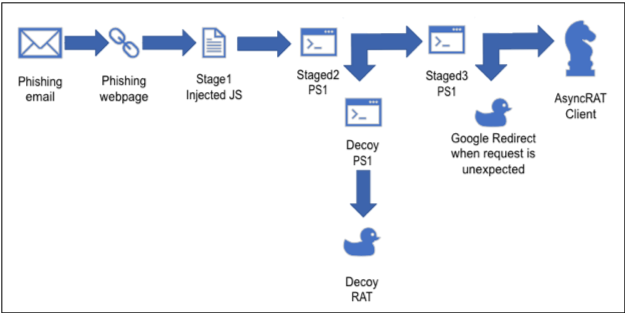
In early September 2023, AT&T Alien Labs recorded a surge in phishing emails targeting specific individuals in specific companies, containing GIF attachments and SVG files, which facilitate the downloading/execution of “highly obfuscated” JavaScript files, PowerShell scripts, and an AsyncRAT client.
AT&T Alien Labs’ cybersecurity researcher Fernando Martinez wrote in the company’s blog post that users on X (formerly Twitter), including reecDeep and Igal Lytzki, reported this peculiarity in the code, prompting the researchers to continue to look for more AsyncRAT samples going as far back as February 2023.
Researchers discovered that the campaign operators, with a focus on firms managing crucial US infrastructure, meticulously selected their targets. To avoid detection, they implemented obfuscation and anti-sandboxing techniques. The strategy involved random generation of variable names and values to enhance detection evasion. Additionally, they adopted a weekly recycling approach for DGA domains and employed redirection decoys to further thwart analysis efforts.
The loader’s modus operandi is spread over multiple stages with strong obfuscation techniques employed to deliver JavaScript files to targeted victims. The payload is delivered through malicious phishing webpages, containing long strings with randomly positioned words.
A similar sample delivering AsyncRAT in March 2023 (reported by Ankit Anubhav) was hidden between Sanskrit characters. However, it employed different TTPs to deliver the final payload indicating that it was part of another campaign.
The code is constantly changing, obfuscated, and randomized, making it hard to detect. Domains like sduyvzeptop and orivzijetop share common characteristics like a Top Level Domain, 8 random alphanumeric characters, a registrar organization, and a country code, raising suspicion.
The Domain Generation Algorithm (DGA) creates a seed based on the day of the year and makes modifications to ensure a new domain is created every seven days, with Sunday being the purposeful generation. The seed is then used to select 15 letters from ‘a’ to ‘n’, with variables (2024 and 6542) changing in scripts for different domain patterns.
AT&T Labs discovered that an organization, Ivan Govno, has registered numerous domains with the Nicenic registrar, some with TLD top and matching attributes. The domains are hosted on BitLaunch (with identifier 399629), known for allowing payments in cryptocurrencies like Bitcoin, Ethereum, or Litecoin, which attracts cybercriminals.
BitLaunch is the cheapest option, but it offers users the option to pay in crypto and get hosted in a more reliable ASN. The DGA domains are hosted on DigitalOcean.
It is worth noting that this campaign is active, with ongoing domain registration and an OTX pulse providing more information. Nevertheless, AsyncRAT is a threat to individuals and organizations and makes it necessary to implement advanced security solutions and increased vigilance against emerging malware strains.
RELATED ARTICLES
- Hackers Stole $59 Million of Crypto Via Malicious Google and X Ads
- Microsoft Disables App Installer After Feature is Abused for Malware
- UAC-0099 Hackers Using Old WinRAR Flaw in Cyberattack on Ukraine
- Fake hotel reservation phishing uses PDF links to spread MrAnon Stealer
- Hacker disrupts Emotet botnet operation by replacing payload with GIFs
[ad_2]
Source link