[ad_1]
Trezor, the hardware wallet manufacturer, has disclosed a data breach involving unauthorized access to a third-party support portal used by the company.
In a worrying development for cryptocurrency enthusiasts, hardware wallet manufacturer Trezor disclosed a data breach on January 20, 2024, that potentially exposed the contact information of nearly 66,000 users.
While the company assures that no user funds were compromised, the incident highlights the importance of cybersecurity even for hardware wallets, which are often touted as the most secure way to store digital assets.
What Happened?
The breach involved unauthorized access to a third-party support portal used by Trezor. The incident occurred on January 17, 2024, and potentially affected users who interacted with the support team since December 2021. The exposed information included email addresses and usernames, however, Trezor confirmed that the attacker did not access the phone numbers or postal addresses of victims.
We are making every effort to work with the third-party service provider to comprehensively investigate the incident. However, our internal audit of the incident suggests potential access to contact details, limited to email and name/nickname.
Trezor
Why is This Concerning?
Even though user funds and addresses remain safe, the exposed contact information puts users at risk of phishing attacks. Hackers could use this information to send targeted emails impersonating Trezor and attempt to steal users’ login credentials or private keys. These keys are essential for accessing and managing cryptocurrency holdings, and if compromised, could lead to significant financial losses.
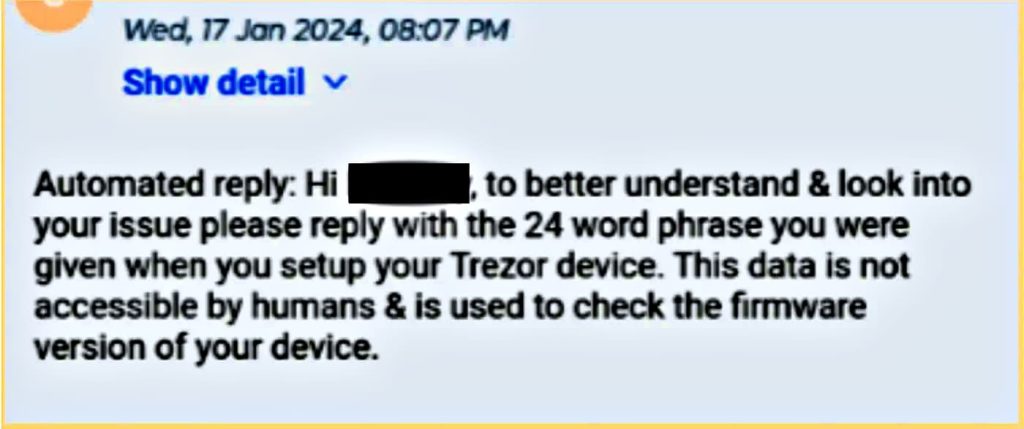
What Trezor is Doing
Trezor has taken several steps in response to the breach:
- Notified all 66,000 potentially affected users via email.
- Emphasized that user funds were not compromised.
- Investigated the incident and took steps to prevent future breaches.
- Advised users to be wary of phishing attempts and to take steps to protect their online accounts.
What Users Can Do
If you are a Trezor user and received an email about the breach, here are some steps you can take to protect yourself:
- Be cautious of any emails claiming to be from Trezor.
- Do not click on any links or open any attachments in suspicious emails.
- Change your Trezor PIN and password immediately.
- Enable two-factor authentication for your Trezor account.
- Regularly update your software and operating system.
- Report any suspicious activity to Trezor support.
Impact of the Breach
The Trezor data breach is a reminder that no system is foolproof, even for hardware wallets. While user funds were not compromised in this incident, it serves as a wake-up call for the cryptocurrency community to be vigilant about cybersecurity. Users should be aware of the risks associated with phishing attacks and take steps to protect themselves.
RELATED ARTICLES
- 6 of the Best Crypto Bug Bounty Programs
- Outdated Wallets Threatening Billions in Crypto Assets
- Crypto Scammers Exploit Gaza Crisis in Donation Scam
- We Need Smarter Smart Contracts To Prevent DeFi Hacks
- Scammers Use Fake Ledger App on Microsoft Store to Steal $800K
- Inferno Drainer Phishing Nets Scammers $80M from Crypto Wallets
- “Get Paid to Like Videos”? This YouTube Scam Leads to Empty Wallets
[ad_2]
Source link
