[ad_1]
So far, the CryptoChameleon phishing scam has successfully phished over 100 victims, with many still active.
Lookout has discovered a multi-pronged phishing campaign, dubbed “CryptoChameleon,” that mimics legitimate login pages for cryptocurrency platforms and the Federal Communications Commission (FCC) via mobile devices.
The kit uses carbon copies of SSO pages and phishing via email, SMS, and voice to trick victims into sharing sensitive information, including usernames, passwords, password reset URLs, and photo IDs, mainly targeting US-based users.
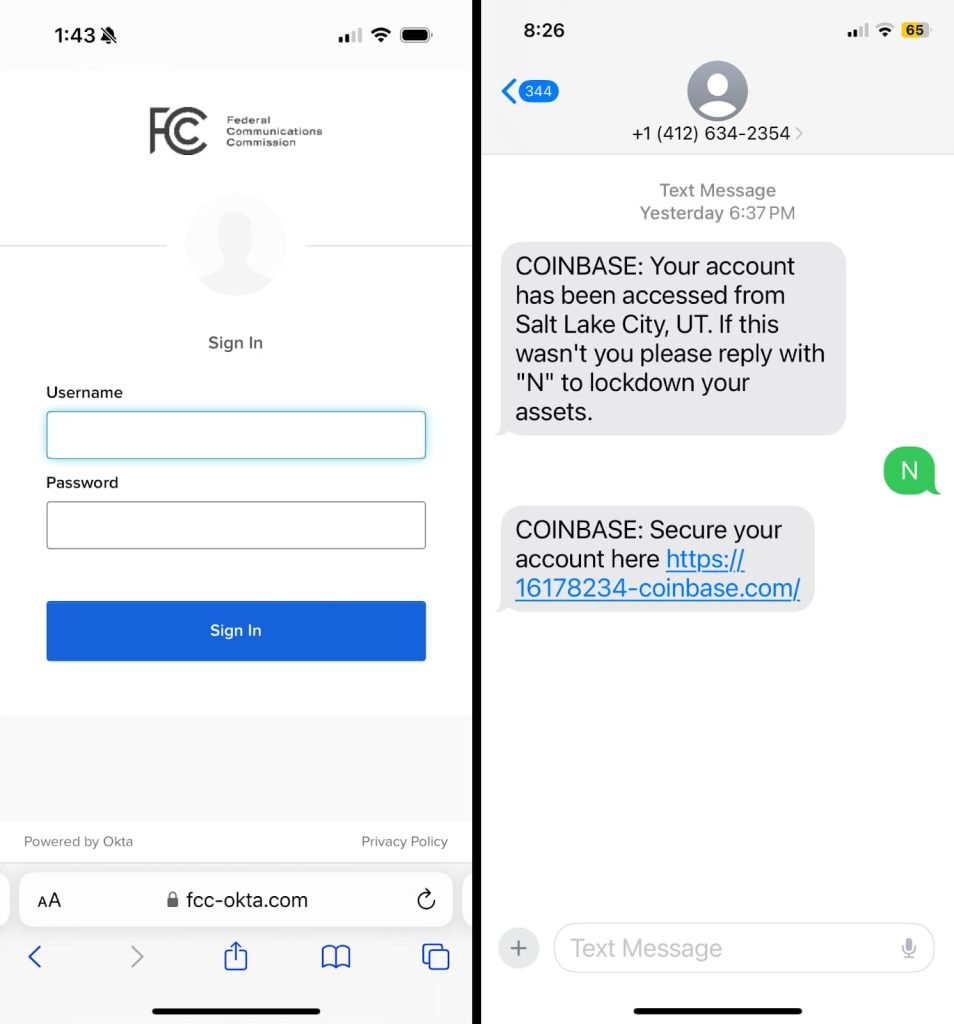
Researchers detected the suspicious phishing kit when they found a suspicious new domain registration, fcc-oktacom. The phishing kit targets cryptocurrency platforms and SSO services and can impersonate various company brands, with Coinbase being the most frequently targeted service. Researchers identified other websites using the kit, with most using a subdomain of official-servercom as their C2.
The attack as reported by Lookout in its blog post, has successfully phished over 100 victims, with many still active. Notable files in the kit include the C2 server URL, client-side logic, and style sheets. Cybercriminals use RetnNet hosting for most sites.
Victims have to first complete a captcha using hCaptcha, which prevents automated analysis tools from identifying the site and creates a sense of credibility for the site. Once done, a login page mimicking the FCC’s official Okta page is launched, where victims enter their credentials and wait for a login or MFA token.
The attacker monitors this page via an administrative console and can select where to send the victim’s information. They try to log in using the victim’s credentials in real-time and redirect them to the appropriate page based on the requested information from the MFA service.
The phishing page could be customized by providing the victim’s phone number and choosing between a 6- or 7-digit code. The phishing kit targets cryptocurrency platforms and SSO services, impersonating various company brands, with Coinbase being the most frequently targeted service.
Additionally, victims are lured through phone calls, emails, and text messages, while phishing emails are disguised as legitimate messages from cryptocurrency platforms or the FCC containing malicious links, while SMS messages resemble legitimate notifications.
Furthermore, Voice phishing involves impersonating representatives to trick victims into revealing confidential information over the phone. Most legitimate victim data came from iOS and Android devices, indicating the attack is primarily targeted at mobile devices.
Researchers suspect that Scattered Spider could be behind this attack because Scattered Spire also impersonates Okta, registers domains using companyname-okta.com, and homoglyph swapping. However, the phishing kit has significantly different capabilities and C2 infrastructure.
CryptoChameleon is a unique phishing campaign that targets multiple devices, mimics genuine login pages, and uses advanced techniques like hCaptcha to bypass detection tools and enhance the legitimacy of their websites, making them difficult to distinguish from legitimate ones.
Researchers suggest users be cautious with unsolicited messages, verify the source of messages, and avoid sharing sensitive information online. Moreover, users must use strong, unique passwords, and stay informed on the latest phishing tactics and best practices for online security.
Experts Opinion
For insights, we reached out to Jason Soroko, Senior Vice President of Product at Sectigo, a Scottsdale, Arizona-based provider of comprehensive certificate lifecycle management (CLM) who stressed moving from traditional login and password and providing cybersecurity training and social engineering to employees.
“Neither the usage of fake login screens nor lookalike domain names is novel, however, each of these techniques is effective in harvesting username and password credentials. What security teams should be doing is getting away from username and password authentication. If this isn’t possible, we have to go back to fundamental training in social engineering.”
“We have been taught not to open attachments in emails that have specific characteristics, however, people also need to be taught to scrutinize the domains of websites they are entering credentials into. Ideally, we must get away from weak forms of authentication that can be harvested this way,” Jason advised.
RELATED TOPICS
- EvilProxy Phishing Kit Hits 100+ Firms, Bypasses MFA
- Russian Hackers Employ Telekopye Toolkit in Phishing Attacks
- NPM Typosquatting Deploys r77 Rootkit via Legitimate Package
- Storm-1283 Sent 927K Phishing Emails with Malicious OAuth Apps
- Telekopye Toolkit Used as Telegram Bot to Scam Marketplace Users
[ad_2]
Source link
