[ad_1]
The Pwn2Own 2024 hacking contest saw a record-breaking first day as participants exposed critical vulnerabilities in Tesla vehicles, popular browsers, and operating systems – This highlights the ongoing challenge of securing our technology and the importance of bug bounty programs.
The Pwn2Own 2024, a hacking contest organized by Trend Micro’s Zero Day Initiative in Vancouver, saw participants earn over $700,000 on the first day through successful exploits against Tesla cars, browsers, and Linux and Windows systems.
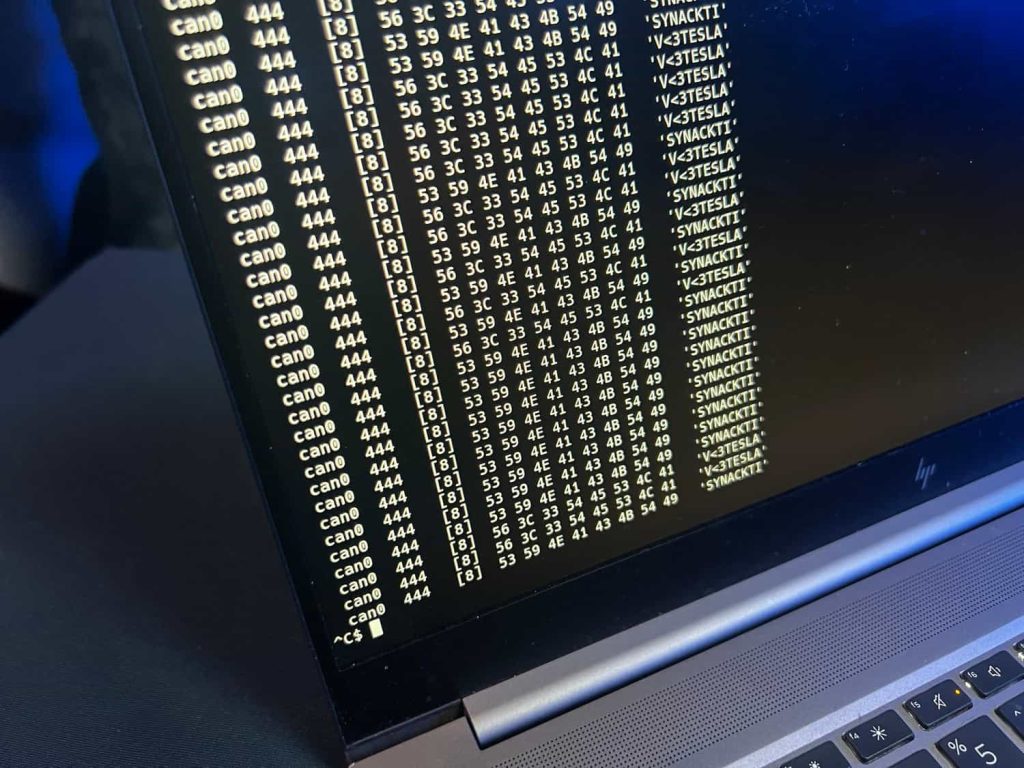
French cybersecurity firm Synacktiv’s hackers earned $200,000 for an integer overflow exploit targeting the Tesla ECU with CAN bus control and also won a new Tesla Model 3. It is worth noting that this was the only scheduled hacking attempt for Tesla cars for this contest.
However, this isn’t the first time Synacktiv has dominated Pwn2Own – they previously won a car in Pwn2Own Automotive 2024.
About the Vulnerability
While the specific details of the exploit remain undisclosed, as per Pwn2Own rules to allow for vendor patching, the competition organizers confirmed that a single integer overflow flaw was used. This vulnerability allowed the team to gain control of the Tesla’s CAN BUS, a crucial communication system within the car. Synacktiv exploited a Tesla ECU with Vehicle (VEH) CAN BUS Control using a single integer overflow flaw to secure their second victory in Pwn2Own competitions.
Day One Highlights
On day one of the Pwn2Own contest, participants were awarded $732,500 by ZDI for reporting 19 unique zero-day vulnerabilities. Here’s the breakdown of the rewards.
Independent white-hat hacker Manfred Paul received $102,500 for remote code execution on Apple Safari using an integer underflow bug, and a PAC bypass exploiting a flaw in the same browser. Paul also executed a double-tap exploit on Chrome and Edge browsers using a rare CWE-1284 vulnerability in round two of the competition.
South Korean team Theori earned $130,000 by combining an uninitialized variable bug, a use-after-free (UAF) vulnerability, and heap-based buffer overflow to escape a VMware Workstation and execute code as system on Windows OS.
Oracle VirtualBox was targeted by REverse Tactics researchers, earning $90,000 and two researchers received $20,000 for their respective Oracle VirtualBox exploits.
Other Pwn2Own participants earned rewards for Chrome and Edge, Safari, Adobe Reader, Windows 11 local privilege escalation, and two Ubuntu local privilege escalation exploits.
Seunghyun Lee, AbdulAziz Hariri, and the Devcore Research team successfully exploited Google Chrome, Adobe Reader, and Windows 11 bugs, earning them $60,000, $50,000, and $30,000 respectively. Lee successfully executed an exploit on Google Chrome, Hariri completed a code execution attack, and the Devcore Research team successfully executed a local privilege escalation (LPE) attack.
Participants will attempt to hack various software on the second day, including VMware Workstation, Oracle VirtualBox, Firefox, Chrome, Edge, Ubuntu, Windows 11, and Docker Desktop. The three-day event is offering a total of $1.3m in cash and prizes.
RELATED TOPICS
- Whitehat hacker bypasses SQL injection filter for Cloudflare
- Hackers Crack Tesla Twice, Rake in $1.3 Million at Pwn2Own
- White hat hackers infect Canon DSLR camera with ransomware
- Whitehat hacker shows how to detect hidden cameras in hotels
- White hat hacker infects smart coffee machine with ransomware
[ad_2]
Source link