[ad_1]
In this campaign, attackers have used the legitimate ChatGPT for Google extension and added malicious code to it in order to steal Facebook session cookies.
The cybersecurity researchers at Guardio have found a new info-stealing campaign exploiting ChatGPT, the popular AI chatbot from OpenAI. In this campaign, attackers are distributing fake ChatGPT extensions that promise to integrate the chatbot with your Google search results. In reality, it can steal your Facebook account.
The latest ChatGPT scam should not come as a surprise, as cybercriminals have been attempting to exploit the popularity of the AI chatbot since its launch last year. In January 2023, it was reported that several fake ChatGPT clone apps on the iOS and Play Stores were collecting user data and sending it to remote servers.
Fake ChatGPT Extension Discovered
In the newly discovered campaign, Guardio researchers noted that it is based on an open-source extension containing malicious code to force the product to function as per the attacker’s demands and make it difficult to detect it.
The fake extension is leveraged by the Chrome Extension API to obtain active Facebook cookies and send the data to the attacker’s server. Hackers can easily log into the victim’s Facebook account, change account credentials and create zombie accounts by converting profiles into a false persona “Lily Collins.” The accounts are then used to distribute malicious ads and propaganda campaigns.
How Does the Attack Work?
Attackers have used the legitimate ChatGPT for Google extension and added malicious code to it in order to steal Facebook session cookies. Users are lured to download the extension via fake sponsored search results.
When the user search for ChatGPT 4, you will click on a sponsored search result that will redirect you to a landing page offering to embed the chatbot inside your search results. After you have installed the extension from the official Chrome Web Store, it allows you access to ChatGPT in search results along with compromising your Facebook account.
“Looking at the “OnInstalled” handler function that is triggered once the extension is installed, we see the genuine extension just using it to make sure you see the options screen (to log in to your OpenAI account). On the other hand, the forked, turned malicious, code is exploiting this exact moment to snatch your session cookies,” the report read.
How to Identify Fake Extension?
Researchers explained that the fake add-on was most probably downloaded via a sponsored ad in Google search results for Chat GPT 4, just like Bitwarden and Radeon users were targeted earlier in 2023. This extension was downloaded from the Chrome Store between Feb 14 and Mar 22.
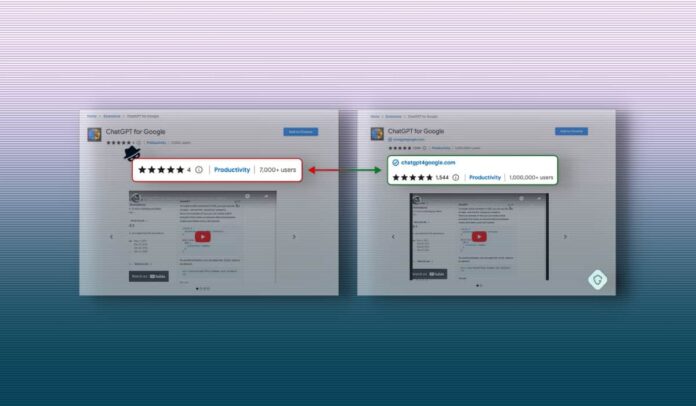
It has now been removed from the store. You can check if the ChatGPT for Google installed on your computer is fake or legit by clicking on the puzzle icon on the Chrome address bar’s right side. then click on Manage Extension> Details> View in Chrome Web Store.
If the official extension shows chatgpt4googlecom as its verified developer and boasts more than a million users then it is original else it is fake.
RELATED NEWS
[ad_2]
Source link