[ad_1]
Millions of users of Tile, one of the leading Bluetooth location-tracking device vendors, may have had their personal information exposed following a recent data breach, which has led to a ransom demand.
According to 404 Media, the hacker gained access to internal company tools using the stolen credentials of a former Tile employee and accessed multiple Tile systems to steal sensitive data.
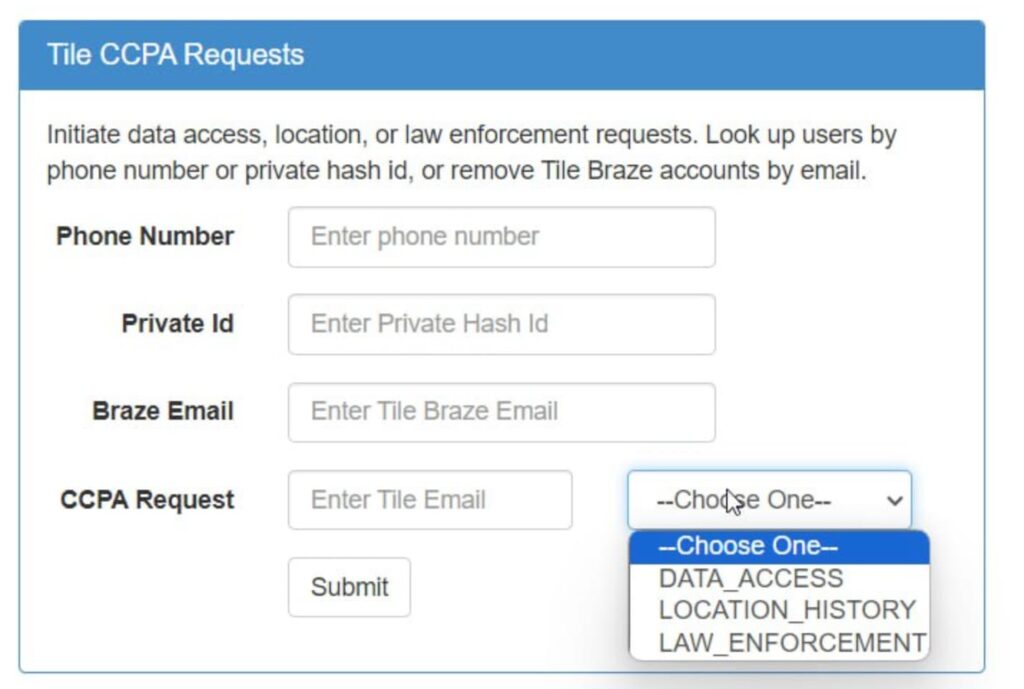
This data included tools used for transferring ownership of the Tile tracker, creating admin accounts, and sending user notifications, as shown in screenshots also provided by the actor.
Location data-focused Life360, the parent company of Tile, announced on June 11th, 2024 that it had detected unauthorized access to its customer support platform. According to the company’s press release, Tile was targeted by a “criminal extortion attempt,” where an unknown actor informed them about possessing Tile’s customer information.
The company immediately investigated and discovered unauthorized access to a Tile customer support platform, but not the Tile service platform. While the company assures users that no financial data, passwords, or location information was compromised as the platform never stored this data, sensitive user data may be exposed, including names, physical addresses, email addresses, phone numbers, and Tile device identification numbers.
“We believe this incident was limited to the specific Tile customer support data described above and is not more widespread,” Life360 CEO Chris Hulls stated, reinstating their commitment to protecting customer information and taking steps to protect their systems from bad actors.
It is worth noting that the press release is not available to users outside the United States therefore a screenshot of it is available below:
The company has reported the incident and extortion attempt to law enforcement. Nevertheless, this breach highlights the vulnerability of companies that track people’s locations and how they can become targets for hackers.
Tile users should be cautious of phishing attempts, as email addresses were exposed. Be wary of emails asking for personal information or login credentials. Monitor your accounts for suspicious activity on email and bank accounts associated with your Tile account.
Experts Comments
Piyush Pandey, CEO at Pathlock, a Flemington, New Jersey-based identity and access security provider commented on the data breach pointing out multiple factors involved including the potential threat carried out by former or disgruntled employees and lack of security authentication.
”In this instance, it appears that access was given using the admin credentials of a former Tile employee, which points to a key tenant of identity security – the ability to have proactive visibility to the access and entitlements of users throughout the joiner, mover, leaver portions of the identity lifecycle.”
”It also seems that there was a lack of multi-factor authentication, which may have thwarted access being granted with just a username and password. This breach also points to the criticality of securing service account access in addition to the primary line-of-business applications,” added Piyush.
Callie Guenther, Senior Manager, Cyber Threat Research at Critical Start highlighted the significant threat intelligence implications after the data breach including targeted extortion, supply chain vulnerabilities, data sensitivity, incident response, etc. Callie also advised to implement the following measures to protect administrator accounts:
- Multi-Factor Authentication (MFA): Require MFA for all admin accounts to add an extra layer of security.
- Strong Password Policies: Enforce the use of strong, unique passwords and regular password changes.
- Least Privilege Principle: Grant admin rights only to those who need them, minimizing the number of users with high-level access.
- Regular Audits and Monitoring: Continuously monitor and audit admin account activities to detect and respond to suspicious behavior promptly.
- Security Awareness Training: Educate employees on recognizing phishing attempts and the importance of safeguarding credentials.
RELATED TOPICS
[ad_2]
Source link