[ad_1]
The notorious Chinese Smishing Triad gang, known for its SMS phishing attacks against Pakistan, the US, and European nations, has now set its sights on iPhone users in India. The group is exploiting iMessage and the government-owned India Post in a sophisticated phishing scam.
FortiGuard Labs has revealed a sophisticated Smishing (SMS Phishing) campaign targeting users of India Post, the country’s government-operated postal system. The scam, attributed to a China-based threat actor known as the Smishing Triad, involves sending deceptive iMessages to iPhone users, claiming that a package is waiting for them at an India Post warehouse.
The fraudulent messages often contain a short URL leading to a fake website designed to mimic the official India Post site. Victims are then prompted to provide sensitive personal information, such as their name, residential address, email ID, and phone number. In some cases, the scammers even request credit card details under the guise of a small redelivery fee.
FortiGuard Labs’ investigation revealed that between January and July 2024, over 470 domain names were registered to impersonate India Post’s official domain. Notably, 296 of these domains were registered through a Chinese registrar, Beijing Lanhai Jiye Technology Co., Ltd., raising concerns about the intentions behind the campaign.
The Smishing Triad has previously targeted other regions, including the US, UK, EU, UAE, KSA, and Pakistan. Their modus operandi involves using third-party email addresses, such as Hotmail, Gmail, or Yahoo, to create Apple IDs and send phishing messages via iMessage. This tactic allows the scammers to bypass traditional email security measures and reach users directly on their iPhones.
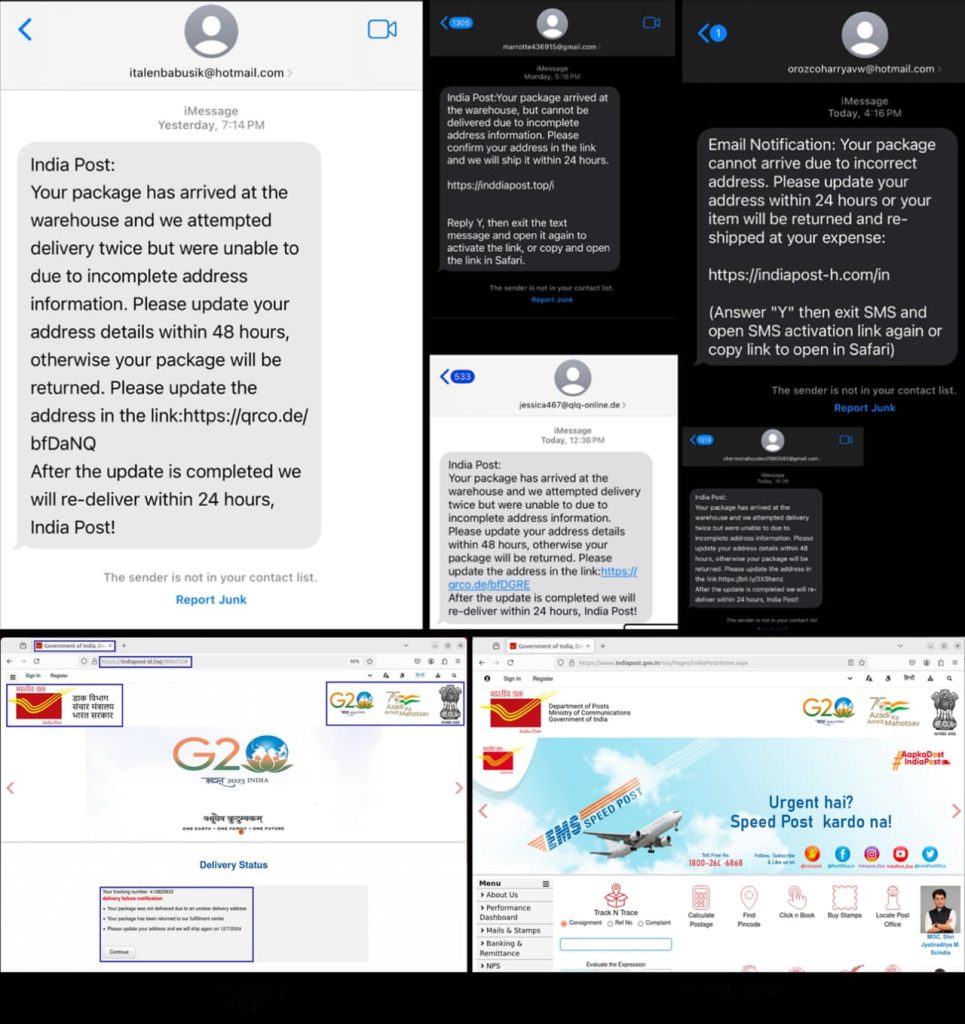
According to Fortinet Labs’ report shared with Hackread.com ahead of its publication on Thursday, the phishing campaign is quite sophisticated and well planned. The investment in registering the malicious domain names alone exceeds USD 1500.
Jason Soroko, Senior Vice President of Product at Sectigo, commented on the issue, stating, “The use of third-party email addresses on iMessage facilitates these attacks, highlighting a need for increased awareness and robust security measures among users to mitigate potential financial losses and data breaches.”
Stephen Kowski, Field CTO at SlashNext Email Security+, emphasized the need for comprehensive mobile web threat protection, stating, “As smishing attacks become increasingly sophisticated, organizations must prioritize educating their users on how to identify and report suspicious messages, while also implementing robust security measures that can inspect and mitigate threats in real-time, regardless of the communication channel used.”
To protect themselves from such scams, users are advised to be cautious of unexpected emails or messages, verify URLs before clicking on them, and avoid sharing personal information via email or messaging apps. Enabling multi-factor authentication and keeping software up to date can also help strengthen account security.
RELATED ARTICLES
- Chinese APT Posing as Cloud Services to Spy on Cambodia
- Chinese Hackers Stole 60K US State Dept Emails from Microsoft
- Chinese Smishing Triad Gang Hits US Users in Cybercrime Attack
- Chinese Scammers Exploit Cloned Websites in Gambling Network
- How Chinese Hackers Stole Signing Key to Breach Outlook Accounts
[ad_2]
Source link
