[ad_1]
The North Korean hacker, Rim Jong Hyok, is accused of being part of the government-backed cyberespionage group Andariel, which is known for conducting attacks on the healthcare, hospital, defence, aerospace, nuclear, and engineering sectors.
On July 25, 2024, the US Department of Justice indicted an individual named Rim Jong Hyok associated with North Korean cyberespionage group Andariel, tracked by Microsoft as Onyx Sleet.
Hyok was indicted by a Kansas City grand jury for a conspiracy to hack and extort US hospitals, launder ransom proceeds, and fund further computer intrusions into defence, technology, and government entities worldwide. The ransomware attacks hindered patient care.
Onyx Sleet, first detected by Microsoft in 2014, has been targeting organizations in the defence, aerospace, nuclear, and engineering sectors across India, South Korea, and the United States to steal sensitive information. It also exploits online gambling websites for financial gain, possibly on behalf of North Korea or individual members.
Microsoft’s investigation with the FBI revealed that Andariel was targeting South Korean educational institutions, construction companies, and manufacturing organizations in May 2024.
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a warning about Andariel, aka DarkSeoul, Silent Chollima, and Stonefly/Clasiopa. It is operated by the North Korean government’s Reconnaissance General Bureau (RGB) 3rd Bureau, which funds its activities through ransomware attacks on US healthcare facilities.
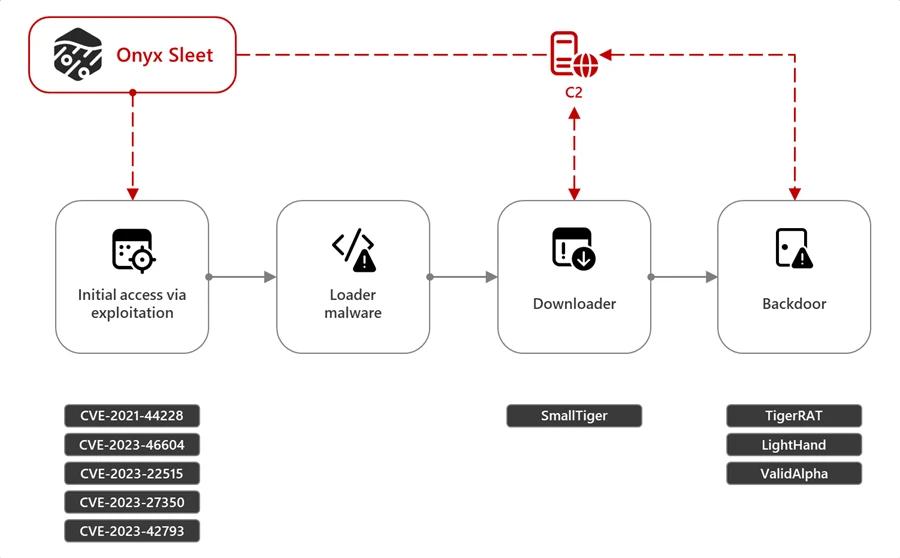
Onyx Sleet or Andariel is a persistent cyber-espionage threat using custom tools and malware to gain access to victim systems. They exploit vulnerabilities in web server software like Log4j, deploy a web shell and gain access to sensitive information and applications.
Additionally, they use system discovery techniques, Scheduled Tasks, and credential-stealing tools like Mimikatz to extort privileges. They also use custom malware implants, remote access tools, and open-source tools for execution and data exfiltration.
Additionally, phishing is conducted using malicious attachments like LNK files or HTA script files in unencrypted/encrypted .zip archives. Once they have access, the group can steal data, disrupt operations, or deploy ransomware.
Andariel has used TigerRAT and SmallTiger and exploited N-day vulnerabilities in its recent attacks. In October 2023, they used the TeamCity – CVE-2023-42793 vulnerability in a targeted attack.
In 2019, the US Department of the Treasury announced sanctions against three North Korean state-sponsored cyber groups, Lazarus, Bluenoroff, and Andariel, for their cyber activity on critical infrastructure. The Treasury vowed to act against these groups, allegedly supporting illicit weapon and missile programs.
Microsoft has found links between Andariel and Storm-0530, another group of actors originating from North Korea.
“Both groups were observed operating within the same infrastructure and were involved in the development and use of ransomware in attacks in late 2021 and 2022,” Microsoft noted.
These attacks highlight the ongoing threat posed by North Korean cyber actors. Organizations must stay alert and implement strong cybersecurity measures to protect themselves.
RELATED TOPICS
[ad_2]
Source link