[ad_1]
The email hack allowed hacktivists to extract highly sensitive documents, along with the personal details of the APT28 leader and Russian GRU officer, Lieutenant Colonel Sergey Alexandrovich Morgachev.
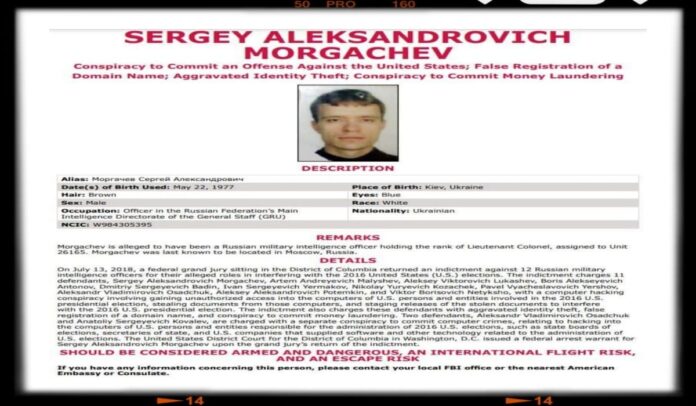
Ukrainian hacktivist group Cyber Resistance, also known as Ukrainian Cyber Alliance, has claimed to have hacked the email, social media, and personal accounts of Russian GRU officer Lieutenant Colonel Sergey Alexandrovich Morgachev (Sergey Aleksandrovich Morgachev). The information was shared with a volunteer intelligence community called InformNapalm.
Notably, Cyber Resistance, the same group mentioned in a previous report by Hackread.com, was involved in a recent hack of Russian Colonel Sergey Valeriyevich Artoshchenko’s email accounts. The hack was carried out by convincing his wife and several other military wives to participate in a patriotic photoshoot while wearing their husbands’ uniforms.
Morgachev, a Kyiv native, is the leader of APT28, Russia’s most notorious hacking group, and simultaneously worked for Russia’s Main Intelligence Directorate of the General Staff of the Russian Army (GRU).
This unit comprises officers of the GRU’s 85th Main Special Service Center military units #26165 and #74455. Morgachev is wanted by the Federal Bureau of Investigation (FBI) for his involvement in devastating cybercrimes globally.
APT28, also known as Pawn Storm and Fancy Bear, directly reports to the Russian military intelligence agency and has carried out cyberattacks against high-profile entities in various countries including the USA, Italy, Germany, Estonia, The Netherlands, Czech Republic, Norway, Poland, and Ukraine. APT28 made headlines during the 2016 US elections after hacking the servers of the US Democratic Party.
In 2016, APT28 was also involved in phishing attacks against authorities investigating the MH17 crash and was accused of posing as ISIS to send death threats to US army wives in 2018.
The hacking of Morgachev’s accounts was carried out by gaining access to his personal account on the government services portal, where the hackers verified the data they had previously obtained from document scans and his current residence and place of service addresses.
According to InformNapalm, the hackers also accessed Morgachev’s AliExpress account and ordered goods for him, including souvenirs featuring the FBI’s logo and adult toys, using his card for payment. The hacktivists confirmed that one parcel is on its way to the recipient. They also hacked Morgachev’s social media accounts.
The hacktivists shared Morgachev’s private correspondence with InformNapalm volunteers, who then released the data into the public domain. The compromised documents included three scanned copies of Morgachev’s personal documents, including Form 4 and passport, as well as his fresh medical certificate dated 13 December 2022, which is required for security clearance to access classified documents.

This incident highlights the increasing threat posed by Cyber Resistance and other Ukrainian hacktivist groups to Russia’s critical infrastructure, government, and non-government entities.
[ad_2]
Source link