[ad_1]
Zyxel informed its customers about the security flaw on 25 April 2023 and announced patches for impacted firewalls, which included USG Flex, ATP, ZyWALL/USG, and VPN.
A variant of the Mirai botnet has successfully hacked various Zyxel Firewalls after exploiting a newly patched operating system command injection vulnerability (CVE-2023-28771). The bug has affected many Zyxel network devices, and now that the Mirai botnet is controlling it, the problem can worsen as it can lead to launching DDoS attacks.
According to Palo Alto Networks’ Unit 42 researchers, who analyzed the downloaded samples, the Mirai botnet sample hacking Zyxel firewalls is called IZ1H9, which was discovered in August 2018. Researchers dubbed it the most active of all Mirai variants.
The botnet client first inspects the network portion of the compromised device’s IP address and avoids execution for a specific list of IP blocks. This includes government networks, tech firms, and internet providers.
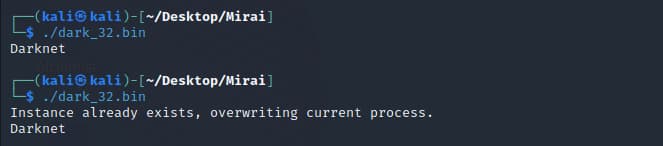
The malware prints “Darknet” onto the console to make its presence felt. It also can ensure the device runs just one instance of the malware. If a botnet process is found on the device, the Mirai botnet client will terminate its current process and start a new process from its list of processes belonging to other variants of the Mirai botnet and other families.
Any product running vulnerable firmware can be exploited even if the user configures the VPN or is in a default state. Mirai operators now own various Zyxel SMB VPN Boxes.
How Was the Bug Discovered?
The vulnerability impacting Zyxel devices was discovered by Trapa Security. It occurred due to inappropriate message handling features in some firewalls that could allow an unauthorized actor to remotely execute OS commands by transmitting specially designed packets to the device. The Internet Key Exchange – IKE is the vulnerable component, explained a report from Rapid7.
Zyxel informed its customers about the security flaw on 25 April 2023 and announced patches for impacted firewalls, which included USG Flex, ATP, ZyWALL/USG, and VPN.
Users Must Immediately Patch Devices
CVE-2023-28771 was patched in April 2023. However, many users have yet to apply the fix, leading to this mass exploitation of vulnerable devices. Researcher Kevin Beaumont informed about the mass exploitation of this vulnerability by the Mirai botnet variant on Thursday, impacting several SMB appliances.
Security experts have urged Zyxel network services users to patch the flaw immediately. A few days back, Rapid7 had warned about the possibility of the bug being exploited in the wild. They do not claim that 42,000 instances of internet-exposed web interfaces of Zyxel devices have surfaced. But Rapid7 researchers believe the number of compromised devices may be much higher. The Mirai malware targeting Zyxel firewalls is distributed as a Unix and Linux executable in linkable format (.elf).
Zyxel is a Taiwanese networking device manufacturer. The company recently fixed two more flaws impacting its firewalls- CVE-2023-33009 and CVE-2023-33010. Both buffer overflow flaws can let an adversary launch a DoS attack or execute arbitrary code on the device.
RELATED ARTICLES
[ad_2]
Source link