[ad_1]
Around half a dozen fake accounts were discovered on GitHub, and several were found on Twitter. All of them used headshots of renowned security researchers and hosted zero-day exploits.
Supply chain attacks could be highly destructive if the target is as high-profile and widely used as GitHub. Cybersecurity researchers at VulnCheck have discovered a supply chain attack targeting GitHub and Twitter.
According to their report, multiple accounts on GitHub and Twitter claim to distribute PoC (proof-of-concept) exploits for zero-day exploits in popular software. However, these are fake accounts, and the PoCs deliver malware.
Campaign Discovery
VulnCheck discovered this campaign in May 2023 when it checked a GitHub repository hosting code that the author claimed was a zero-day for the Signal app. The next day, they discovered another account offering a WhatsApp zero-day.
Researchers kept finding bogus accounts throughout May 2023, all offering zero-day exploits for apps such as Google Chrome, Signal, Microsoft Exchange Server, and Discord. Later in May, researchers came across similar accounts on Twitter.
Around half a dozen fake accounts were discovered on GitHub, and several were found on Twitter. All of them used headshots of renowned security researchers and hosted zero-day exploits.
Beware of Fake Accounts on GitHub, Twitter
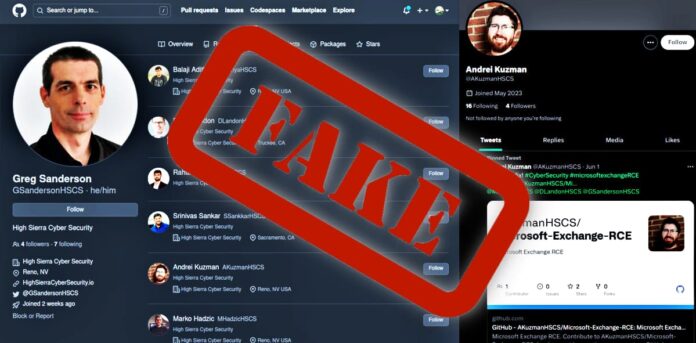
According to VulnCheck, unidentified threat actors have created a network of fake accounts on GitHub and Twitter that appear to be associated with cybersecurity researchers. To generate credibility for these accounts, the threat actors have used profile pictures of actual security researchers.
Researchers have noted that these fake repositories are promoted as part of a non-existent firm called High Sierra Cyber Security. Each account features a headshot, Twitter handle, associated organization, followers, a link to the company’s website, and a hidden, malicious repository.
Malicious Objectives Behind Fake Accounts
These fake accounts distribute a Python script through which a malicious binary is downloaded and executed on the device. It is worth noting that the malware can work on both Windows and Linux-based systems. GitHub accounts have been suspended, but Twitter accounts remain online.
What are the Dangers?
Researchers believe that this supply chain attack is very elaborate and can have serious consequences. The SolarWinds attack is one of the most devastating supply chain attacks, affecting many public and private sector agencies and causing extensive damage. A malware-infected software was responsible for this attack.
Considering that GitHub is the world’s largest open-source code repository, the consequences of this particular supply chain attack could be even more drastic. Injecting malicious code into a repository or compromising it can impact various software used by countless endpoints. Attackers can deploy malware to steal sensitive data, perform identity theft, or launch ransomware attacks and wire frauds.
Researchers are unclear whether this is an experiment or a campaign. Nevertheless, it is essential to be cautious when accessing untrusted sources for executing code. Check the full list of fake accounts here.
RELATED ARTICLES
[ad_2]
Source link