[ad_1]
According to ESET’s researchers, components of FontOnLake malware are divided into three groups: Trojamized app, Rootkit, and Backdoor.
Researchers at Slovak cybersecurity company ESET have identified a new malware family utilizing custom and well-designed modules. In ESET’s white paper [PDF], researchers revealed that the malware dubbed FontOnLake Rootkit malware targets Linux systems and its modules are under active development.
The malware samples uploaded to VirusTotal indicate that the first intrusion through this previously unidentified threat happened in May 2020. Tencent, Lacework Labs, and Avast are also tracking this malware using the moniker HCRootkit.
We have found a new #Linux #malware leveraging an open source kernel-mode rootkit #Suterusu and we dubbed it #HCRootkit. 1/7
— Avast Threat Labs (@AvastThreatLabs) August 25, 2021
About FontOnLake
Researchers noted in their report that FontOnLake has a “sneaky nature,” “advanced design,” and “low prevalence.” Therefore, it is easier to use this malware in targeted attacks.
According to ESET researcher Vladislav Hrčka, it allows remote access to the attackers, can serve as a proxy server, and steal credentials. This malware family uses “modified legitimate binaries” to collect data, and these binaries have been adjusted to load more components.
Moreover, to stay undetected, the malware uses a rootkit. These binaries are used on Linux systems but “can additionally serve as a persistence mechanism,” Hrčka wrote in a blog post.
Likely Targets
The information about its C&C server’s location and the countries where the samples were uploaded indicates that the campaign targets users in Southeast Asia.
ESET researchers further stated that they have discovered two versions of the Linux rootkit based on the Suterusu open source project and perform similar functions such as:
- File hiding
- Hiding itself
- Process hiding
- Performing port forwarding
- Hiding network connections
- Exposing the collected credentials to its backdoor
- Magic packets reception (These packets instruct the rootkit to download and execute another backdoor)
“We believe that FontOnLake’s operators are particularly cautious since almost all samples seen use unique C&C servers with varying non-standard ports. The authors use mostly C/C++ and various third-party libraries such as Boost, Poco, or Protobuf. None of the C&C servers used in samples uploaded to VirusTotal were active at the time of writing – which indicates that they could have been disabled due to the upload,” researchers explained.
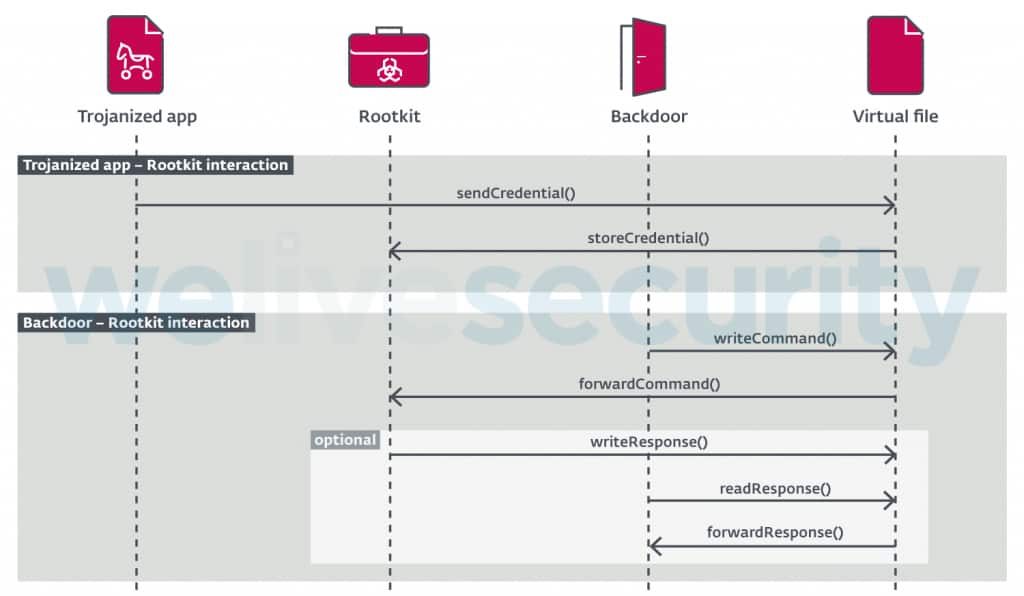
Known Components
As shown in the screenshot above; FontOnLake malware’s known components are divided into three groups: Trojanized applications are the modified legitimate binaries adjusted to conduct a range of malicious activities.
The second component is user-mode backdoors that serve as the main communication point for the malware operators. Thirdly, it has Rootkits, which are kernel-mode components used to provide fallback backdoors and assist with updates.
“Their scale and advanced design suggest that the authors are well versed in cybersecurity and that these tools might be reused in future campaigns,” Hrčka wrote, adding that most of the features are designed to hide FontOnLake’s presence, offer backdoor access, and relay communication, researchers concluded.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.
[ad_2]
Source link