[ad_1]
- MMRat is a new Android banking trojan targeting Southeast Asian users.
- It is distributed through phishing websites disguised as official app stores.
- It uses a customized Protobuf-based C2 protocol to improve its performance.
- It captures screenshots, controls devices, collects extensive device, personal data.
- Users can protect themselves from MMRat by downloading apps from trusted sources and avoiding suspicious websites.
Cybersecurity researchers at Trend Micro Mobile Application Reputation Service (MARS) have discovered a stealthy new Android trojan targeting Southeast Asian mobile phone users since late June 2023.
This Android banking trojan, dubbed MMRat due to its distinctive package called com.mm.user, features a long list of capabilities as it can capture screenshots, remotely control victims’ devices, monitor user input, and perform many other tasks apart from bank fraud while staying undetected.
MARS researchers wrote in a blog post published on August 29, 2023, that the malware remained undetected on VirusTotal.
How is MMRat Distributed?
Most MMRat samples were downloaded from phishing websites disguised as official app stores in different languages to expand their reach. It is worth noting that researchers couldn’t determine how victims were lured into visiting these fake app stores.
This “potent” malware has been declared a “considerable threat” to mobile phone users. It uses a specially designed, fully customized Protobuf-based C2 protocol, a rare feature in Android banking trojans. This feature improves the malware’s performance while transferring large data volumes.
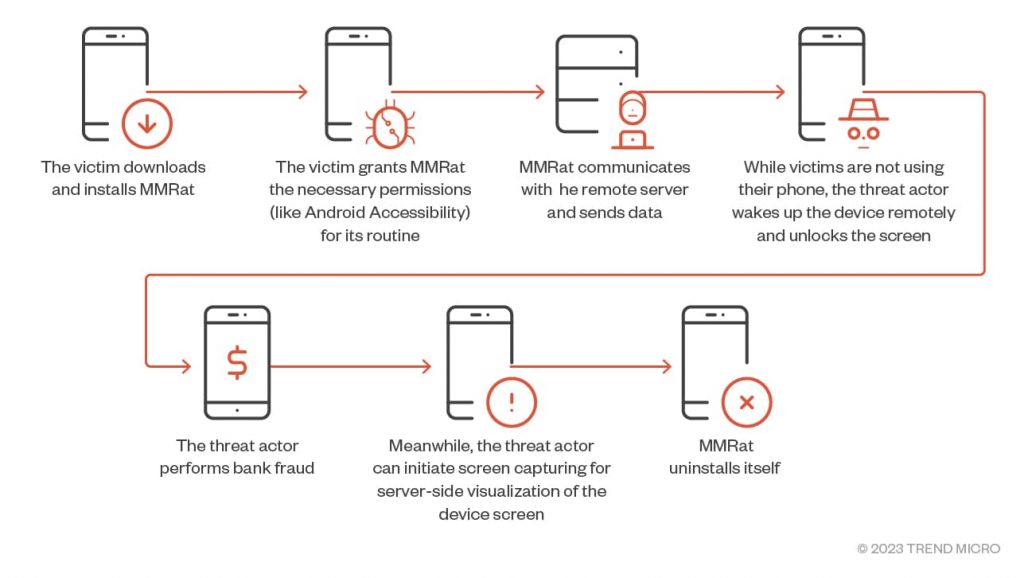
Attack Sequence
MMRat’s primary focus is on conducting bank fraud. The attack relies on the victim downloading and installing the malware on their device and granting it the required permissions. Once done, the malware quickly establishes communication with its remote server, sending copious amounts of data, including personal and mobile data, keylogging data, device status, etc.
Moreover, the malware operator can remotely turn on the device when not in use, unlock the screen, and carry out bank fraud. They may also capture screens for server-size visualization. After performing its malicious tasks, MMRat can self-uninstall and remove every trace of the manipulation.
MMRat Capabilities
As mentioned above, MMRat is a highly capable malware that can capture user input/screen content and allow remote control of the device. Relying on the Android Accessibility service and MediaProjection API for its functioning, the malware can easily detect when the device is on or off and reboot it by registering a receiver on the system.
Furthermore, the trojan avoids suspicion by disguising itself as an official government or dating app and enters the victim’s device through a phishing website. It also launches a 1×1-sized pixel activity to stay persistent.
What Data Does it Collect?
According to Trend Micro’s blog post, MMRat can collect extensive device and personal data such as screen and battery data such as whether the screen is locked and current activities, installed apps, contact lists, and network data, e.g., signal strength and network type.
The Android trojan also schedules a time task to collect data at regular intervals. This timer executes every second, and the counter resets every 60 seconds. It looks for victims’ contact lists and installed app info to get maximum personal details.
After obtaining Accessibility permission, it can obtain extended permission and modify device settings by bypassing user intervention. It is also interested in lock screen patterns, which it collects when the victim unlocks the device and sends it to the C2 server so that the malware operator can unlock the device when desired.
What’s worse, it captures real-time screen content and streams it to a remote server via the MediaProjection API. MMRat also uses the “user terminal state” approach for capturing screen data, in which it doesn’t record the screen as a video but dumps the child nodes in Windows every second.
How to Stay Protected?
Users must download apps from trusted platforms like Google Play Store or Apple App Store and avoid suspicious websites posing as app stores. It is equally important to keep updating device software to mitigate security threats like MMRat. Lastly, be very careful when granting Accessibility permissions to an app.
RELATED ARTICLES
[ad_2]
Source link