[ad_1]
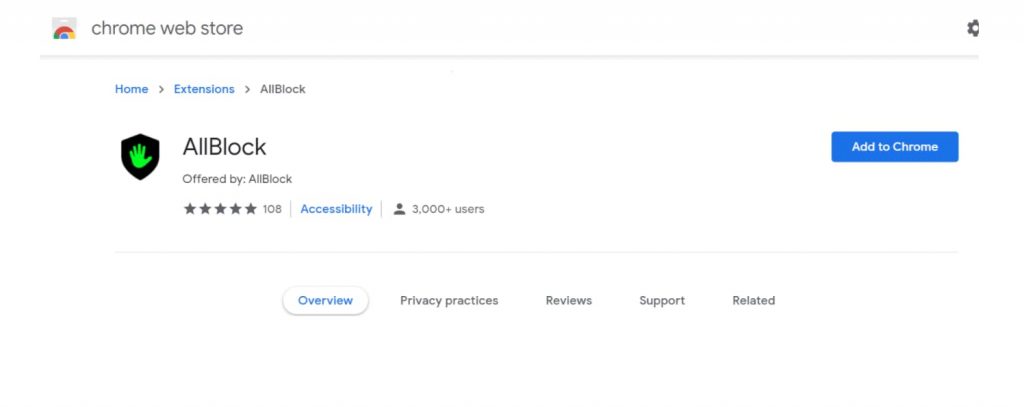
AllBlock was available on Google Chrome’s Web Store where it is marketed as a potent Ad Blocker focusing on Facebook and YouTube to prevent pop-ups.
Google has maintained that it takes the security of Chrome extensions very seriously and regularly vets them to prevent exploitation. However, the new report from Imperva reveals that maybe Google isn’t performing its job as sincerely as it claims to be.
Chrome’s Ad-Blocker Extension Displaying Ads on Google
Security vendor Imperva’s Sillam and Ron Masas reported that a Google Chrome extension called AllBlock designed to block ads is injecting ads into Chrome and Opera.
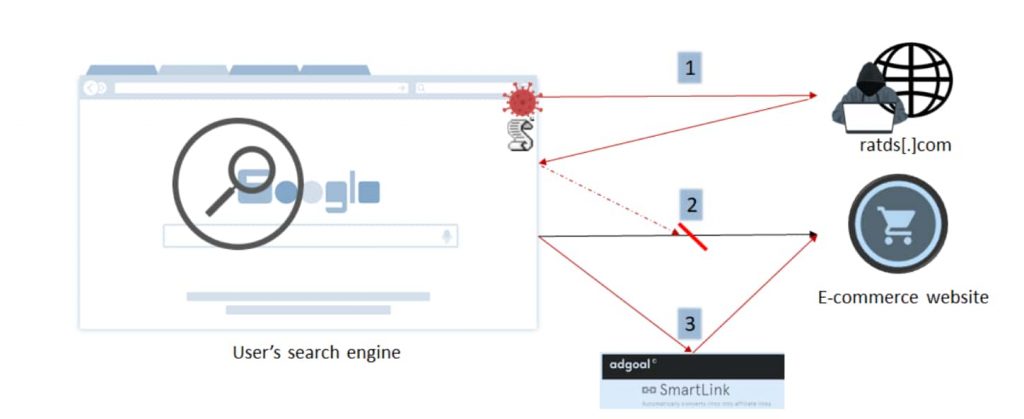
Although the extension blocks ads, it runs a script in the background that injects a piece of JavaScript code into every tab that the user opens. This code communicates to remote servers and download/installs a payload connected to an ad-injection scam’s operators.
“When the user clicks on any modified links on the webpage, he will be redirected to an affiliate link. Via this affiliate fraud, the attacker earns money when specific actions like registration or sale of the product take place,” Imperva researchers observed.
The payload then retrieves a series of unwanted ads, most of which are not from legitimate sources, and includes affiliate links. AllBlock was available on Google Chrome’s Web Store where it is marketed as a potent Ad Blocker focusing on Facebook and YouTube to prevent pop-ups. It has now been removed from Opera add-ons and Chrome Web Store.
What is Ad Injection?
Ad injection is a method of inserting ads or links into a web page that isn’t supposed to host them. Scammers can earn money from advertisements by injecting unrelated ads or redirect unsuspecting users to affiliate links to earn a commission.
Imperva researchers identified such a campaign in August 2021 where several previously unknown domains were found to be distributing an ad injection script that would send legit URLs to a remote server and, in response, obtained a list of redirection domains. Consequently, when a user clicked on an altered link, they were redirected to another page, usually an affiliate link.
Ad injection scripts may feature evasion techniques like excluding Russian search engines, active detection of Firebug variables, and clearing the debugging console after every 100ms. In AllBlock ad injection scam, Imperva researchers were able to find the script in bg.js that they had been looking for since August.
How is The Extension Marketed?
It is yet unclear how AllBlock is distributed or promoted. According to Imperva, scammers are probably using other extensions in this campaign. They couldn’t identify the origin of the attack because of the way the malicious script was injected.
“The script we first observed was injected via a script tag pointing to a remote server where the AllBlock extension injects the malicious code directly to the active tab,” Imperva’s report revealed.
This indicates a larger campaign at work using different delivery methods and extensions, which might be connected with the PBot campaign.
Did you enjoy reading this article? Like our page on Facebook and follow us on Twitter.
[ad_2]
Source link