[ad_1]
The new 0-Day vulnerability was actively exploited by the Winter Vivern cyberespionage group before its discovery and subsequent patch by Roundcube, a web-based IMAP email client, with ESET’s report.
The Russian cyberespionage group Winter Vivern (aka TA473, and UAC-0114), known for its persistent attacks on European and Central Asian governments, has once again made headlines. ESET, a Slovak cybersecurity firm, has recently revealed the group’s utilization of a 0-day (zero-day) cross-site scripting (XSS) vulnerability in the Roundcube Webmail server, signaling an alarming escalation in their tactics.
ESET researchers, who have been closely monitoring Winter Vivern’s activities for over a year, discovered the exploitation of this new vulnerability on October 11th, 2023. This XSS vulnerability, identified as CVE-2023-5631, allowed attackers to remotely compromise Roundcube Webmail servers, a popular email platform.
Notably, this vulnerability is distinct from CVE-2020-35730, a previously exploited flaw by the same group, as outlined in ESET’s research.
Targeted Entities
The campaign orchestrated by Winter Vivern focused on Roundcube Webmail servers belonging to governmental entities and a think tank, all situated within Europe. This is in line with the group’s primary objective of targeting government institutions and organizations in Europe and Central Asia.
Modus Operandi
Winter Vivern is infamous for employing a variety of tactics to infiltrate their targets, including the use of malicious documents, phishing websites, and a custom PowerShell backdoor. While there is a low level of confidence, ESET researchers suggest a potential connection between Winter Vivern and MoustachedBouncer, a Belarus-aligned group.
Since at least 2022, as reported by Hackread.com, Winter Vivern has been known to target Zimbra and Roundcube email servers owned by governmental entities. Additionally, the group exploited CVE-2020-35730, another XSS vulnerability in Roundcube, in August and September 2023.
It is worth mentioning that Winter Vivern is not the only threat actor exploiting Roundcube vulnerabilities. Sednit (also known as APT28) has been seen using the same XSS vulnerability in Roundcube, occasionally targeting the same victims.
The Exploited Vulnerability (CVE-2023-5631)
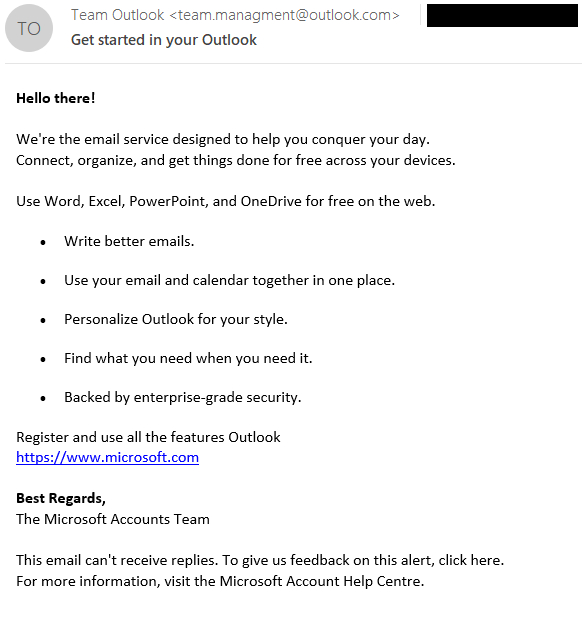
This XSS vulnerability, according to ESET’s blog post, could be exploited remotely by sending a specially crafted email message. In this particular campaign, the emails were sent from the address team.managment@outlookcom with the subject line “Get started in your Outlook.”
The malicious email appeared ordinary at first glance, but upon examining the HTML source code, a concealed SVG tag containing a base64-encoded payload was revealed. The payload was concealed within the onerror attribute of an image tag in the SVG. When decoded, this payload led to the execution of JavaScript code in the victim’s browser.
Surprisingly, the JavaScript injection worked even on fully patched Roundcube instances. The vulnerability was traced back to the server-side script rcube_washtml.php, which did not adequately sanitize the malicious SVG document before incorporating it into the HTML page interpreted by the user.
ESET researchers reported the issue to Roundcube, and the vulnerability was patched promptly on October 14th, 2023. The affected Roundcube versions include 1.6.x before 1.6.4, 1.5.x before 1.5.5, and 1.4.x before 1.4.15.
Implications and Conclusion
Winter Vivern’s transition to a 0-day vulnerability is a clear indication of their determination to infiltrate high-value targets. Despite the group’s relatively unsophisticated toolset, they remain a significant threat to European governments. Their success can be attributed to their persistent phishing campaigns and the prevalence of outdated, vulnerable applications used by targeted organizations.
In response to ESET’s discovery, the Roundcube team acted swiftly to address the vulnerability. A disclosure timeline reveals that the vulnerability was reported on October 12, and the necessary patches were released just two days later, ensuring the security of Roundcube Webmail servers.
ESET Research commended the Roundcube developers for their rapid response and collaboration in resolving the issue. It is vital that organizations and government entities keep their software up to date to mitigate the risk of such attacks in the future.
RELATED POSTS
- ProtonMail Code Vulnerabilities Leaked Emails
- APTs Exploiting WinRAR 0day Flaw Despite Patch Availability
- Email Hacking Reigns as Top Cybersecurity Threat, Indusface Study
- Russian Hackers Employ Telekopye Toolkit in Broad Phishing Attacks
- Mozilla Rushes to Fix Critical Vulnerability in Firefox and Thunderbird
- EvilProxy Phishing Kit Targets Microsoft Users via Indeed.com Vulnerability
[ad_2]
Source link