[ad_1]
Do not install these three apps; they are still listed in the Google Play Store
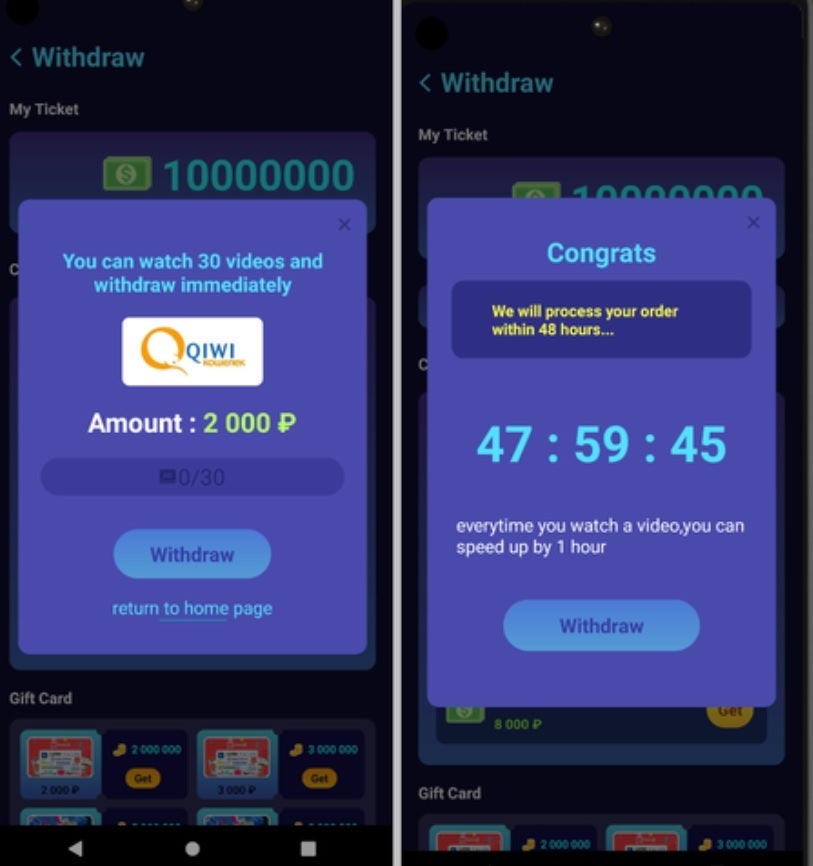
The report from Dr.Web points out that these rewards are often impossible to receive as users must accumulate a large number of rewards before being forced to watch dozens of commercials in order to cash out. After watching all of those ads, users were advised to watch even more to “speed up” the rewards process. The report states that even after all that “the apps did not verify any of the payment-related data provided by users, so the chances of receiving any of the money promised from these apps are extremely small.”
- Lucky Step – Walking Tracker with 10 million downloads.
- WalkingJoy with 5 million downloads.
- Lucky Habit: health tracker with 5 million downloads.
All three apps connect with the same command & control server. Such servers are usually used by attackers to send directions to systems infected by malware. With all three apps communicating with the same remote server, it is apparent that they have the same developer. It is also pointed out that earlier versions of the Lucky Step-Walking Tracker falsely said that users had the option of converting their rewards into gift cards for various online stores.
Do not install these three apps on your Android device
The Lucky Step-Walking Tracker app was eventually updated and the functionality that would convert rewards into cash was removed and the interface elements that would be tapped to make this conversion disappeared. All previously accumulated rewards instantly became worthless.
The one thing you can do to protect yourself from installing malicious apps
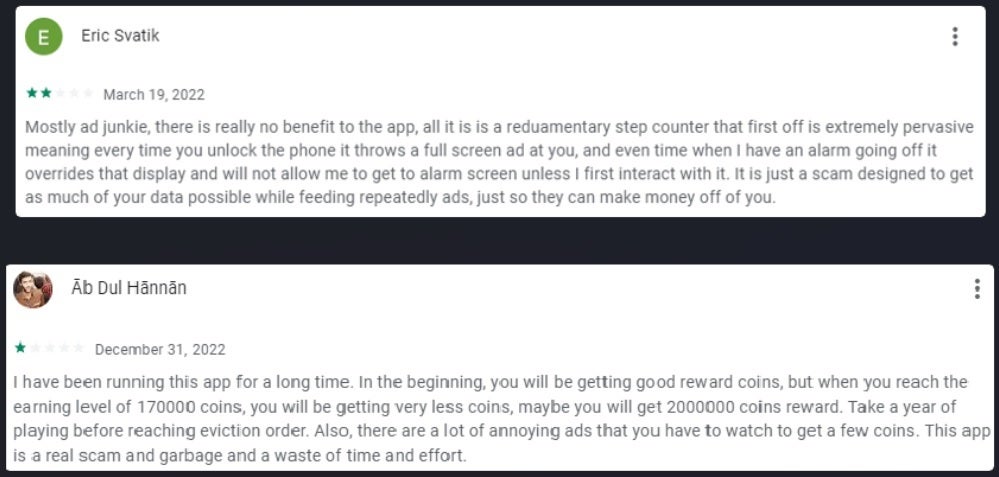
If you’re a long-time PhoneArena reader, you know that we tell you to read the comments section before installing an app from a developer that you’re not familiar with-even if the app is listed in the Play Store. That is where you will find red flags that can warn you to stay away from a certain app. For example, two comments written by a pair of unlucky Android device users who installed the Lucky Step – Walking Tracker app contained plenty of red flags.
These two comments from the listing for the Lucky Star app contain enough red flags to keep you from installing it
One comment came from a user who gave the app two stars (!!??!!) while stating that it is “Mostly ad junkie, there is really no benefit to the app…every time you unlock the phone it throws a full-screen ad at you…when I have an alarm going off it overrides that display and will not allow me to get to [the] alarm screen unless I first interact with it. It is just a scam designed to get as much of your data possible while feeding repeatedly ads just so they can make money off of you.”
This is how these three apps trick you into watching dozens and dozens of ads
A second comment gives the app one star and says, “Also, there are a lot of annoying ads that you have to watch to get a few coins. This app is a real scam and garbage and a waste of time and effort.”
We just punched up these apps in the Google Play Store so if you see them, do not install any of the three on your Android devices. Also, if you’ve already installed any of the three, uninstall them immediately.
Here’s one more malicious app that you need to avoid
Dr.Web’s report also mentioned a fitness app called FitStar that creates a customized weight-loss plan for 29 rubles (equivalent to 41 U.S. cents). However, what those subscribing didn’t know was that the program they were signing up for was good for only one day. At the end of the trial, subscribers were automatically signed up for four days of service for an additional 980 rubles (equivalent to $13.86). Full access to the program cost 7,000 rubles ($98.98) and the app continued to automatically extend users’ subscriptions every four days.
This app is also still listed in the Google Play Store. Comments for this app note that if you install it, the icon doesn’t show up on your phone’s list of installed apps making it hard to uninstall. The same review also notes that “The app is trying from the start to get into either Facebook or Google data…”
[ad_2]
Source link
