[ad_1]
Android and Windows users, beware of fake online meeting sites such as Google Meet, Zoom, and Skype, infecting devices with malicious malware like SpyNote RAT for Android, NjRAT, and DCRat.
Zscaler’s ThreatLabz cybersecurity researchers have discovered a new scam where Remote Access Trojans (RATs) are distributed through online meeting platforms, targeting Android and Windows users with malware. The purpose is to distribute malware that can steal sensitive data and control infected devices.
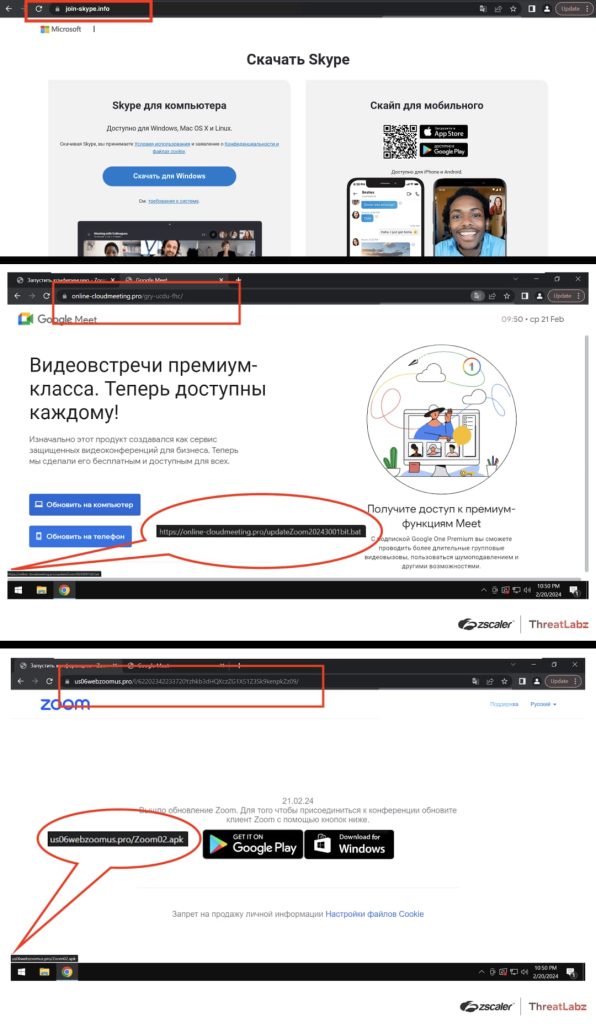
Researchers discovered a threat actor creating fraudulent websites for spreading malware, including SpyNote RAT for Android and NjRAT and DCRat for Windows, in December 2023. These RATs can steal confidential information and log keystrokes. Users are lured through fake online meeting sites impersonating brands like Skype, Google Meet, and Zoom.
The actor used shared web hosting, hosting all fake sites on a single IP address in Russian, and URLs that closely resembled the actual websites. The attackers distributed multiple malware families using these fake websites, posing a significant threat to innocent users.
To download the software, users must either click the Android or Windows buttons. When they click on Android, a malicious APK file gets downloaded, whereas clicking on the Windows button triggers the download of a BAT file, which automates tasks and performs additional actions, such as downloading a RAT payload.
A campaign imitating legitimate online meeting platforms is a significant threat, with fake sites mimicking their appearance and functionality. In December, as noted by Zscaler in a blog post, a fake Skype site, join-skypeinfo, was created to trick users into downloading the application, leading to a BAT file and a WinRAR archive file.
The fake Google Meet site, online-cloudmeetingpro, was hosted on a subpath resembling a joining link. The fake Zoom sites have URLs with genuine Zoom meeting IDs that increase the risk of falling victim to the scam.
These fake websites also contained an open directory with NjRAT executable files, suggesting the attacker may use them in other campaigns.
Such campaigns can have devastating consequences. RATs can compromise devices, allowing attackers to steal sensitive information, monitor user activity, and potentially control the infected device.
To protect yourself, double-check URLs, verify meeting invitations, download software from official sources, and use antivirus and anti-malware software. Beware of fake websites, verify meeting invitations, and download applications from official sources.
RELATED TOPICS
- Konni RAT Exploiting Word Docs to Steal Data from Windows
- Fake Chrome Browser Update Installs NetSupport Manager RAT
- Bifrost RAT Variant Targets Linux Devices, Mimics VMware Domain
- AsyncRAT Infiltrates Key US Infrastructure Through GIFs and SVGs
- Popular Android Screen Recorder iRecorder App Revealed as Trojan
[ad_2]
Source link