[ad_1]
FIN7, a notorious cybercrime gang, is back with a new bag of tricks! Learn about FIN7’s evolving tactics, including ransomware and custom EDR bypass tools like AvNeutralizer. Discover how to fortify your defences against FIN7 with expert tips from Sentinel Labs’ research.
Russian hackers are shifting their tactics, now opting for paid tools instead of the custom tools they have traditionally been known for. This trend is evident in the activities of the Russian cybercrime gang FIN7, which has been targeting financial institutions and businesses worldwide for over a decade.
Notorious for its initial focus on point-of-sale (POS) system breaches, FIN7 has continuously evolved its tactics to maximize its gains. Sentinel Labs’ latest report analyzes the gang’s shift towards ransomware attacks, highlighting their preferred weapons and modus operandi.
According to researchers, FIN7 shifted its focus to ransomware operations in 2020, affiliating with RaaS groups like REvil and Conti and launching its own programs under Darkside and BlackMatter. They created fraudulent infosec firms like Combi Security and Bastion Secure to deceive security researchers. Despite setbacks, FIN7’s activities continue.
Shedding light on FIN7‘s sophisticated toolbox, Sentinel Labs’ found one particularly concerning tool, AvNeutralizer, an EDR impairment tool designed to neutralize security software, rendering systems vulnerable to further attacks.
In November 2022, SentinelLabs reported a connection between FIN7 and the Black Basta group on using AvNeutralizer (AuKill) in ransomware attacks, which they are selling on underground forums now.
Other tools include Powertrash, a heavily obfuscated PowerShell script used by FIN7 to stealthily execute backdoor payloads in their malicious campaigns. Diceloader, aka Lizar or IceBot, is a backdoor that allows attackers to establish a C2 channel, controlling the system by sending position-independent code modules. Diceloader is typically deployed through Powertrash loaders in FIN7 operations.
A helper UI client, the “Remote System Client,” is used to interact with Diceloader C2 servers and control its victims whereas an SSH-based backdoor was found on a server attributed to FIN7, which exposed an open directory web server used as a staging server to serve payloads.
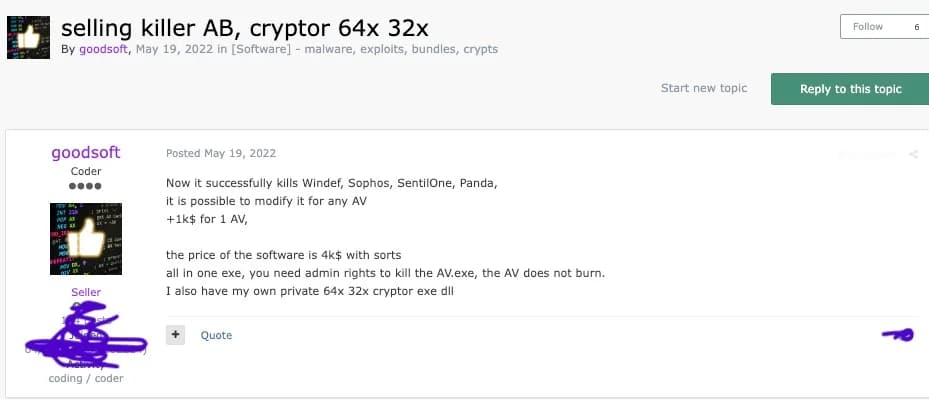
FIN7 uses multiple pseudonyms to hide its identity and sustain its underground criminal operations. Users “goodsoft”, “lefroggy”, and “killerAV” advertised their “PentestSoftware” for $6,500 monthly on the exploitin forum, “Stupor” advertised an AV killer targeting security solutions for $10,000 on the xssis forum. Based on evidence researchers claim that all these users belong to the FIN7 cluster, likely using multiple pseudonyms to maintain their illicit operations.
Fin7 uses automated SQL injection attacks to exploit public-facing applications. They employ a multi-layered approach, including obfuscating their malware code, leveraging legitimate tools for malicious purposes, and exploiting vulnerabilities in popular software. This constant innovation makes it challenging for cybersecurity researchers to track FIN7’s activities and develop effective defences.
To protect against such threats, businesses should regularly update systems and software, implement a layered security approach, educate employees on cybersecurity best practices, and have a data backup and recovery plan.
RELATED TOPICS
- TeamViewer Confirms Security Breach by Russian Midnight Blizzard
- Russian Midnight Blizzard Hackers Breached Microsoft Source Code
- Russian APT28 Exploiting Windows Vulnerability with GooseEgg Tool
- Russian Hackers Hit Mail Servers in Europe for Political and Military Intel
- Russian Ministry Software Backdoored with North Korean KONNI Malware
[ad_2]
Source link
