[ad_1]
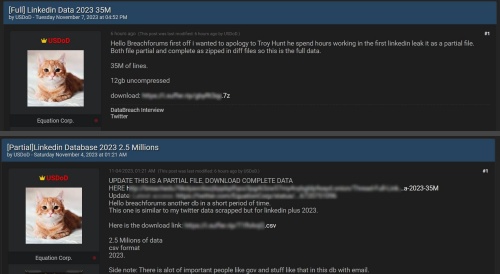
The scraped LinkedIn database was leaked in two parts: one part contained 5 million user records, while the second part contained 35 million records.
A LinkedIn database, holding the personal information of over 35 million users, was leaked by a hacker operating under the alias USDoD. The database was leaked on the infamous cybercrime and hacker platform, Breach Forums.
It is important to note that USDoD is the same hacker responsible for breaching the FBI’s security platform InfraGard last year and disclosing the personal details of 87,000 of its members.
The hacker confirmed in a post on Breach Forums that the most recent LinkedIn database was obtained through web scraping. Web scraping is an automated process utilized by software to extract data from websites, primarily for gathering specific information from web pages.
Regarding the contents of the data, as observed by Hackread.com, the database predominantly comprises publicly available information from LinkedIn profiles, containing full names and profile bios. Although the database contains millions of email addresses, it’s a relief to note that no passwords are included in the leaked data.
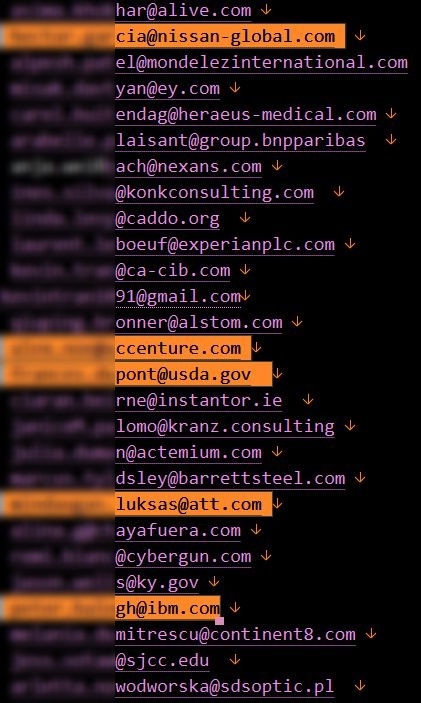
The screenshot below shows email addresses included in the breach belong to high-ranking US government officials and institutions. Additionally, email addresses from various government agencies worldwide have also been identified.
Legitimacy of LinkedIn Data: Authentic or Fraudulent?
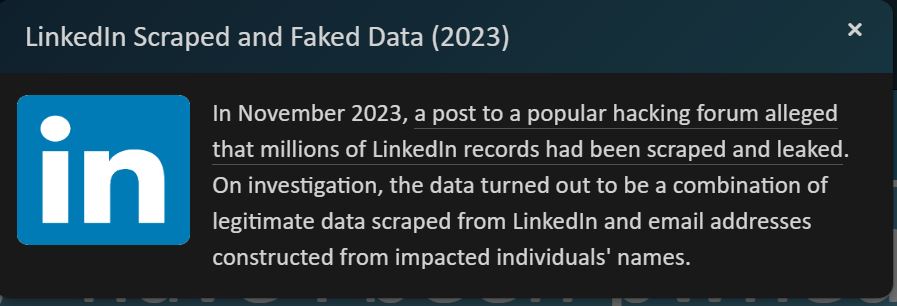
Troy Hunt of HaveIBeenPwned analysed over 5 million accounts from the database and concluded that it includes a mixture of information from various sources such as public LinkedIn profiles, fabricated email addresses, and other sources. Troy emphasizes that while some of the data might be anecdotal or partially fabricated, the people, companies, domains, and many email addresses are real.
“Because the conclusion is that there’s a significant component of legitimate data in this corpus, I’ve loaded it into HIBP,“ Hunt explained. “But because there are also a significant number of fabricated email addresses in there, I’ve flagged it as a spam list which means the addresses won’t impact the scale of anyone’s paid subscription if they’re monitoring domains.“
This however is not the first time when LinkedIn’s scrapped database has been leaked online. In April 2021, a threat actor was selling 2 scraped LinkedIn databases with 500 million and 827 million records. In June 2021, a hacker sold a scrapped LinkedIn database containing data of 700 million users.
RELATED ARTICLES
- Hackers Posed as Israelis in Targeted LinkedIn Phishing Attack
- Twitter Scraping Breach: 209M Accounts Leaked on Hacker Forum
- API Misuse: Hacker Exposes 2.6M Duolingo Users’ Emails & Names
- Meta Fined €265 million in Facebook Data Scraping Case in the EU
- Data scraping firm leaks 235m Instagram, TikTok, YouTube user data
[ad_2]
Source link