[ad_1]
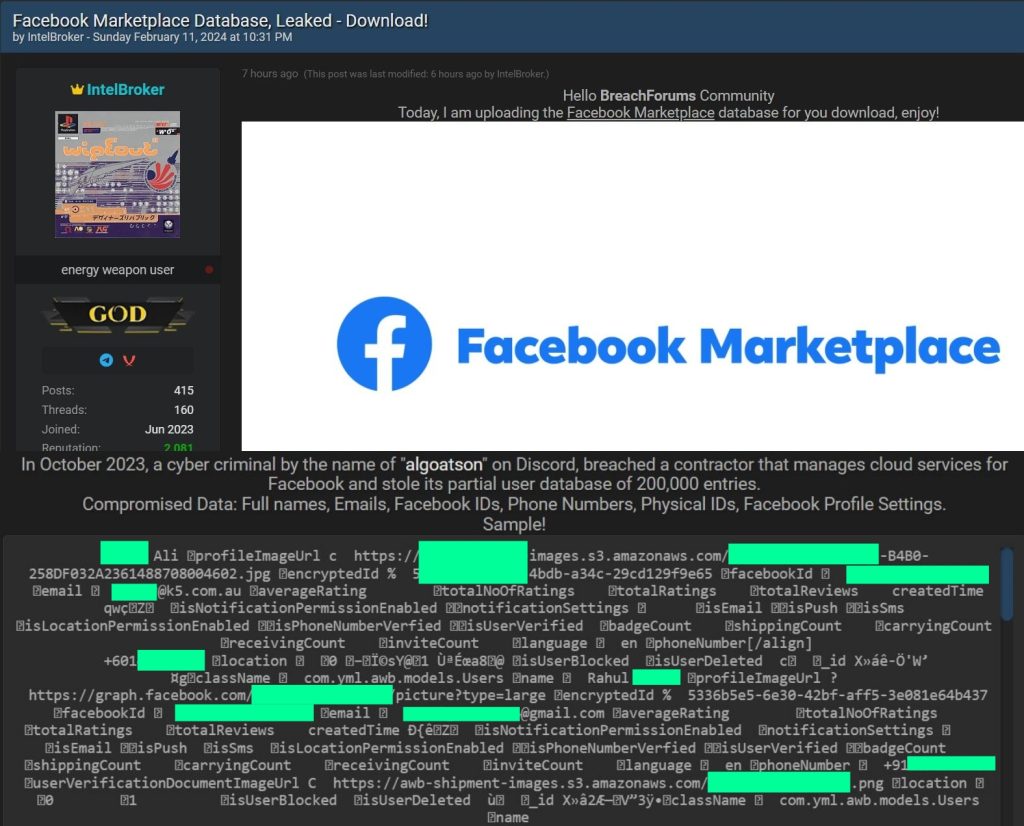
The alleged partial Facebook Marketplace database has been leaked on Breach Forums by the infamous threat actor IntelBroker. They claim that another actor, using the alias “algoatson,” stole the database from a contractor responsible for managing cloud services for Facebook.
The infamous threat actor known as IntelBroker has claimed responsibility for leaking a partial database of the Facebook Marketplace. The alleged breach, apparently conducted by another cybercriminal using the alias “algoatson” on Discord, occurred in October 2023. However, the database was only made public earlier today, on Sunday, February 11, 2024.
According to a post on Breach Forums, IntelBroker disclosed that the hack targeted a contractor responsible for managing cloud services for Facebook. The breach resulted in the theft of approximately 200,000 entries from the user database, compromising sensitive personal information.
It is worth noting that IntelBroker did not disclose the name of the allegedly targeted contractor. Facebook doesn’t utilize a single contractor company to manage all of Facebook Marketplace data. Instead, they leverage a combination of internal teams and external partnerships depending on the specific data aspect.
The compromised data includes full names, Facebook IDs, phone numbers, physical IDs, and Facebook profile settings of the affected users. Hackread.com can exclusively confirm that there are 24,127 email addresses involved in the leak.
The good news is that there are not passwords involved, but the bad news is that this breach potentially exposes Facebook Marketplace users to various forms of identity theft, phishing attacks, and other malicious activities.
IntelBroker
IntelBroker, notorious for their involvement in several high-profile cyber attacks, including the leaking of sensitive US Department of Defense documents in December 2023, has a track record of breaching organizations and selling stolen data on underground forums.
Their previous exploits include the General Electric security breach, which led to the sale of DARPA-related network access in November, 2023, as well as the Weee! Grocery Service hack, where 1.1 million accounts were leaked online in Februrary 2023.
At the time of reporting, attempts to contact “algoatson” via their Discord profile were unsuccessful, as their profile was unavailable. However, efforts to establish communication with the alleged perpetrator are ongoing, and updates will be provided as the situation develops.
META, Facebook and Data Breaches
META’s Facebook has previously made headlines for cybersecurity-related concerns. In April 2021, threat actors leaked the personal data of over 500 million users from 106 countries through web data scraping.
Similarly, in December 2019, hackers exposed the data of 267 million Facebook users on a hacker forum. This breach also stemmed from scraping activities and included users’ full names and email addresses.
In December 2019, another incident occurred where a thief stole unencrypted hard drives containing sensitive data belonging to 29,000 Facebook employees. The data was stored on hard drives within computer equipment owned by a payroll worker, which had been left in the worker’s vehicle.
Nevertheless, the latest alleged leak of the partial Facebook Marketplace database is another example how persistent cybercriminals have become. Facebook, along with alleged affected users, must take immediate steps to mitigate the impact of this breach and enhance security measures to prevent similar incidents in the future.
What’s Next for Users?
Here are five tips for Facebook Marketplace users to protect themselves in the aftermath of the alleged breach:
- Change Passwords and Enable Two-Factor Authentication (2FA): While no passwords were leaked in this incident, users should immediately change their Facebook password and activate two-factor authentication (2FA) to enhance their account’s security. This precautionary measure is crucial, especially if threat actors attempt to exploit passwords obtained from previous data breaches leaked online.
- Monitor Account Activity: Regularly monitor your Facebook account for any suspicious activity, such as unrecognized logins or changes to your account settings. Report any unauthorized activity to Facebook immediately.
- Be Cautious of Phishing Attempts: Watch out for phishing emails, messages, or calls pretending to be from Facebook or other trusted sources. These may attempt to trick you into revealing sensitive information or clicking on malicious links. Avoid clicking on links from unfamiliar or suspicious sources.
- Review Privacy Settings: Review and adjust your Facebook privacy settings to limit the visibility of your personal information. Consider restricting who can see your profile, contact information, and posts on the Marketplace to trusted individuals only. Additionally, consider locking your Facebook profile if the feature is available in your country.
- Watch Out for Voice and SMS Phishing: Besides making sure your account is safe, keep an eye out for scams over the phone or through text messages, which we call vishing and smishing. Scammers might pretend to be someone you trust and try to get you to give away personal info. If you get a call or text asking for sensitive stuff like your bank details, be careful. Don’t click on any links or reply if you’re not sure who it’s from.
Stay tuned for further updates on this developing story.
Note: The authenticity of the leaked database and the identities of the individuals involved are subject to ongoing investigation.
RELATED ARTICLES
- Hacker Leaks 800,000 Scraped Chess.com User Records
- Facebook glitch sent unintended friend requests to users
- Hackers phish 615,000 login credentials by using Facebook ads
- Facebook’s Official Page Hacked; Demand Release of PM Imran Khan
- Chinese firm leaked 200m Facebook, Instagram, LinkedIn users’ data
[ad_2]
Source link
