[ad_1]
Bitdefender researchers and the cybersecurity community speculate that Hunters International might be a revival or successor to the Hive Ransomware, especially in the absence of any reported arrests by the authorities.
Hive, one of the most notorious global ransomware operators, targeted over 1,300 companies and amassed $100 million in ransom payments. However, it was dismantled in January 2023 through a joint operation by the FBI and law enforcement agencies in the Netherlands and Germany.”
However, no arrests were made at the time due to the group’s covert, transnational operations. According to Bitdefender’s research, the group appears to have recommenced its activities under a new name, Hunters International.
Bitdefender’s blog post revealed that Hive’s leadership strategically ceased operations and transferred their remaining assets to Hunters International. This information was initially reported by security researcher @rivitna2 in a post on X (formerly Twitter) on October 20, 2023.
“#Hive is back! Now they are #Hunters International!”
Security researcher Will Thomas @BushidoToken also found startling similarities and code overlaps between both groups’ codes. Thomas reportedly found a 60% match between both sets.
“Ever since the takedown of Hive ransomware by the FBI, it seems the operators have been busy developing their next project: Hunters International. Multiple code overlaps and similarities link Hive and Hunters together, at least +60% match from my research 🔍 h/t @rivitna2.”
While these discoveries seem to confirm that Hunters International is a rebranded version of Hive, the group has refuted these assumptions in a surprising turn. Hunters International maintains that they are an independent entity formed after acquiring and rectifying Hive’s infrastructure and source code.
Their preference lies in data exfiltration rather than data encryption, and the dismantling of Hive provided them with the ideal opportunity to pursue this avenue.
“All of the Hive source codes were sold including the website and old Golang and C versions and we are those who purchased them,” the group stated.
This opportunistic group doesn’t focus on specific regions or industries. Primarily, they target victims in the United States, the UK, Germany, and Namibia including hospitals. The group employs a simplistic approach because it uses fewer command line parameters, has streamlined the process of encryption key storage, and their preferred malware is less verbose.
The gang offer Ransomware-as-a-Service, using Rust language ransomware. Their approaches are rather unique as they don’t embed the encryption key in each file. Instead, they generate two key sets in memory for file encryption and store both as the encrypted drive’s root with a .key extension.
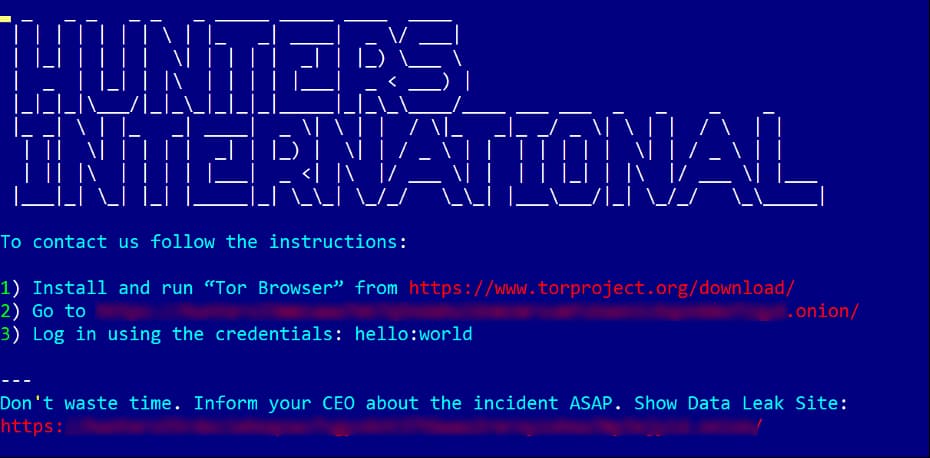
Their ransomware family, identified by Bitdefender’s flagship security platform GravityZone, was Trojan.Ransom.Hunters. Regarding their payment method, the victims have to access a chat portal using the credentials provided in the ransom note.
Whether Hive has resurfaced as Hunters International or not, there’s no doubt that ransomware groups are constantly evolving and developing new techniques. Therefore, extended international cooperation and implementing strong cybersecurity measures are essential to mitigate the threats timely.
RELATED ARTICLES
- FIN8 Resurfaces with New Sardonic Backdoor
- Mamba ransomware that encrypts entire hard drives resurfaces
- BBTok Malware Returns, Targeting Over 40 Banks in Brazil and Mexico
- US-Led Alliance of 40 Countries Unites to Combat Ransomware Threat
- RansomedVC Ransomware Quitting and Selling its Entire Infrastructure
[ad_2]
Source link