[ad_1]
Microsoft urges customers to install Exchange Server security patch and update WinRAR to thwart Forest Blizzard hackers.
In March 2023, Microsoft’s Threat Protection Intelligence team identified a critical vulnerability (CVE-2023-23397) that exposed Microsoft Outlook customers to potential exploitation by threat actors. The vulnerability allowed attackers to steal Net-NTLMv2 hashes and gain access to user accounts.
The vulnerability is caused by a specially crafted email message sent to a user. Upon opening the message, the user’s Net-NTLMv2 hash is transmitted to the attacker, who can subsequently leverage the hash to pilfer the user’s password.
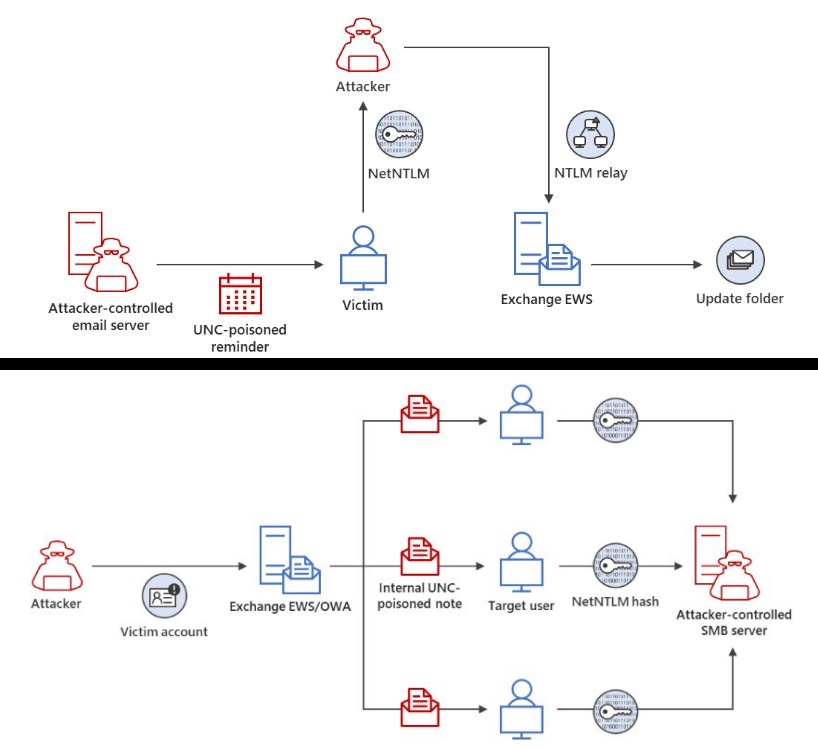
Now, in an updated blog post, the team has revealed that it has found evidence that the vulnerability has been exploited by the threat actor group Forest Blizzard (aka STRONTIUM, APT28, and Fancy Bear) to attack organizations.
For your information, the group is thought to have affiliations with or support from the Russian military intelligence agency. Notably, this is the same group allegedly led by Russian GRU officer Lieutenant Colonel Sergey Alexandrovich Morgachev, whose email address was compromised by the Ukrainian hacktivist group Cyber Resistance in April 2023.
Forest Blizzard is known for its focus on critical infrastructure, including government entities, energy sectors, transportation systems, and non-governmental organizations. Its operations extend to the Middle East, the United States, and Europe.
In its December 4 blog post Microsoft also highlighted that as of September 2023, Forest Blizzard had exploited a 0-day vulnerability in WinRAR, which was initially identified in August 2023 (CVE-2023-38831). By that time, multiple Advanced Persistent Threat (APT) groups had already targeted 130 organizations, successfully pilfering funds from traders.
Despite the availability of a patch for WinRAR’s 0-day vulnerability, threat actors persist in targeting systems that continue to use the unpatched version of the software.
The good news is that Microsoft collaborated with the Polish Cyber Command (DKWOC) to counter Forest Blizzard’s actions. At the time of writing, Microsoft had released a patch for the vulnerability (CVE-2023-23397).
The patch is available for all supported versions of Outlook. Users are urged to install the patch as soon as possible.
Takeaway
Microsoft Exchange customers should promptly install the latest security patches and update to the latest version. Users of WinRAR are also advised to update to mitigate the risk of falling victim to the Forest Blizzard APT group.
In addition to installing the patch, users can also take the following steps to protect themselves from this vulnerability:
- Use a strong password for your Outlook account.
- Be careful about the email messages that you open.
- Enable two-factor authentication for your Outlook account.
- Do not open email messages from unknown senders or email messages that contain attachments.
RELATED ARTICLES
- Fancy Bears Hacked IAAF – Athletes’ Data Stolen
- Fancy Bear’s VPNfilter malware is back with 7 new modules
- Anti-theft software LoJack hijacked by Russian Fancy Bear group
- Ukraine Hacks Russia’s Aviation Agency, Claims “Aviation Cannibalism”
- Fancy Bear Hackers Distributing Graphite Malware using PowerPoint Files
[ad_2]
Source link
