[ad_1]
Alert! Missing NVD Data Leaves Businesses Vulnerable. Patching Delays Due to Disruption. Security Experts Urge Action.
A disruption at the National Institute of Standards and Technology (NIST) is causing problems for organizations that rely on its National Vulnerability Database (NVD). The NVD is a central repository for information about software vulnerabilities, serving as a critical resource for organizations to identify and address security weaknesses in their systems.
Security policies mandate governments and commercial organizations to address vulnerabilities based on NVD-provided severity levels within specific days, making it the world’s most significant vulnerability database.
Therefore, it is concerning that NIST has stopped enriching software vulnerabilities in NVD since February 12, 2024. This significant drop in enrichment was first discovered by software security provider Anchore’s VP of Security, Josh Bressers, and subsequently noted by Cisco Threat Detection & Response’s principal engineer, Jerry Gamblin, Gamblin and NetRise.
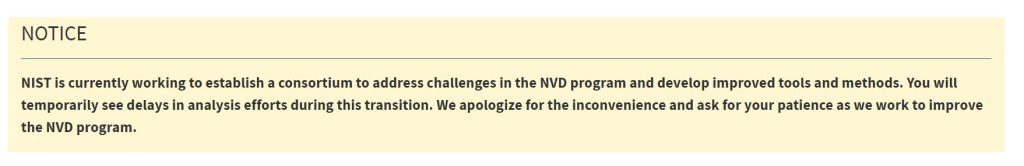
The NVD announced on February 15th that it is working to establish a consortium to address challenges in the NVD program and develop “improved tools and methods.” This may cause temporary delays in analysis efforts, the NVD explained. However, security analysts opine that the NVD is lagging in fully reporting CVEs.
“NIST is currently working to establish a consortium to address challenges in the NVD program and develop improved tools and methods. You will temporarily see delays in analysis efforts during this transition. We apologize for the inconvenience and ask for your patience as we work to improve the NVD program.”
Hackread.com captured a screenshot from the website, which has been displayed since February 14, 2024.
As pointed out by a report referring to NetRise CEO Tom Pace, reported that only 200 out of 2700 Common Vulnerabilities and Exposures (CVEs) have been enriched. This means over 2500 vulnerabilities added to the database have been uploaded without crucial metadata information.
These include the description of the vulnerability and software ‘weakness’ potentially leading to an exploit (called Common Weakness and Exposure/CWE), the names of affected software products, the vulnerability’s criticality/CVSS score, and patching status. Bressers shared an updated graph showing few CVEs have been enriched in the past 30 days.
The issue is attributed to a decrease in CVEs enriched with crucial metadata, such as Common Product Enumerators (CPEs) and criticality scores (CVSS). The NVD has left thousands of CVEs untagged since mid-February, leaving around 40% of this year’s CVEs without vital information. This is concerning as CPE is the main way to match a CVE to a component and relies on many home-grown vulnerability solutions.
For your information, MITRE developed the CVE framework to identify known security flaws. CVE IDs are reported by CVE Numbering Authorities, which include 350 tech companies, security vendors, and researchers.
CVEs are tagged with other cybersecurity acronyms like Common Weakness Enumerators (CWEs), Common Vulnerability Scoring System (CVSS), and Common Platform Enumerator (CPE). CWEs describe coding flaws, CVSS scores describe CVE impact severity, and CPEs identify systems in danger.
This disruption poses a significant challenge to organizations that depend on the NVD for vulnerability management. Without access to this comprehensive data, organizations cannot efficiently identify vulnerable systems within their networks. This can lead to delayed patching or remediation efforts, potentially exposing these systems to exploitation by malicious actors.
The cybersecurity researchers are urging NIST to prioritize resolving this interruption and resume providing complete vulnerability data within the NVD. Transparency regarding the cause of this issue is also essential to ensure continued trust and collaboration within the cybersecurity community.
RELATED TOPICS
- Vulnerability Risk Management for External Assets
- ZombieBoy crypto malware exploits CVEs to evade detection
- NIST’s Cybersecurity Framework 2.0: Guide for All Organizations
- Flashpoint Uncovers 100K+ Hidden Vulnerabilities, Including 0-Days
- Ethical Hackers Reported 835 Vulnerabilities, Earned $450K in 2023
[ad_2]
Source link