[ad_1]
Alarming new research exposes thousands of CSAM (child sexual abuse material) consumers through infostealer malware logs. Recorded Future identifies dark web users with credentials for CSAM.
A new study by Recorded Future’s Insikt Group has identified thousands of individuals who have accessed child sexual abuse material (CSAM) on the dark web, tracked down by analyzing logs from infostealers, a type of malware that steals user information from infected devices.
Infostealer steals sensitive data like login credentials, OS details, autofill data, screenshots, credit card numbers, cryptocurrency wallets, and browsing history through phishing, spam campaigns, fake update websites, SEO poisoning, and malvertising. It creates an infostealer log to store this data and transmits it back to the threat actor’s servers.
The research involved creating a list of high-fidelity CSAM domains, queuing Recorded Future Identity Intelligence proprietary data to identify users with login credentials, and grouping them based on each source.
Collaboration with non-profit organizations like the World Childhood Foundation and Anti-Human Trafficking Intelligence Initiative (ATII) helped determine popular sources where CSAM is hosted and consumed.
Insikt Group analysts used infostealer logs from February 2021 to February 2024 to identify CSAM consumers by cross-referencing stolen credentials with known domains. They identified 3,324 unique credentials used to access known CSAM websites, providing valuable data for law enforcement, including usernames, IP addresses, and system information
Using open-source intelligence (OSINT) and digital artefacts, including cryptocurrency wallet addresses, transaction histories, non-CSAM web accounts, physical addresses, phone numbers, email addresses from browser autofill data, and associations with online services like social media and job application portals they gathered more information about these users.
This is similar to a development by Microsoft. In January 2020, the technology giant announced Project Artemis, aimed at detecting CSAM consumers through online chat using a new tool.
However, in September 2020, a server belonging to the Microsoft Bing search engine exposed a treasure trove of data online, which contained user search queries and location data, including those searching for CSAM and murder. Despite having location data of users involved in criminal searches, the company did not report it to the relevant authorities.
As for Insikt Group, the researchers specifically studied three users from “141 repeat offenders identified over 362 log references,” including a Cleveland, Ohio resident, d****, convicted of child exploitation and accounts on 4 CSAM sites, an Illinois children’s hospital volunteer, docto, with a history of retail theft and accounts on 9 CSAM sites, and a Venezuelan student Bertty, maintaining accounts on 5 CSAM sites and likely involved in the purchase and distribution of CSAM content.
“We were able to rank CSAM hosting websites by the number of compromised credentials in the last three years. The top ten sources1 identified below were kidfl*4m, alice*4, gk*fgh, 243*n, c*ub, *ian, my*eens, 3d*oys, *yboys, and boyvi*,” Recorded Future’s report (PDF) read.
According to researchers, the following three countries had the highest counts of users with credentials to known CSAM communities:
- India
- Brazil
- United States
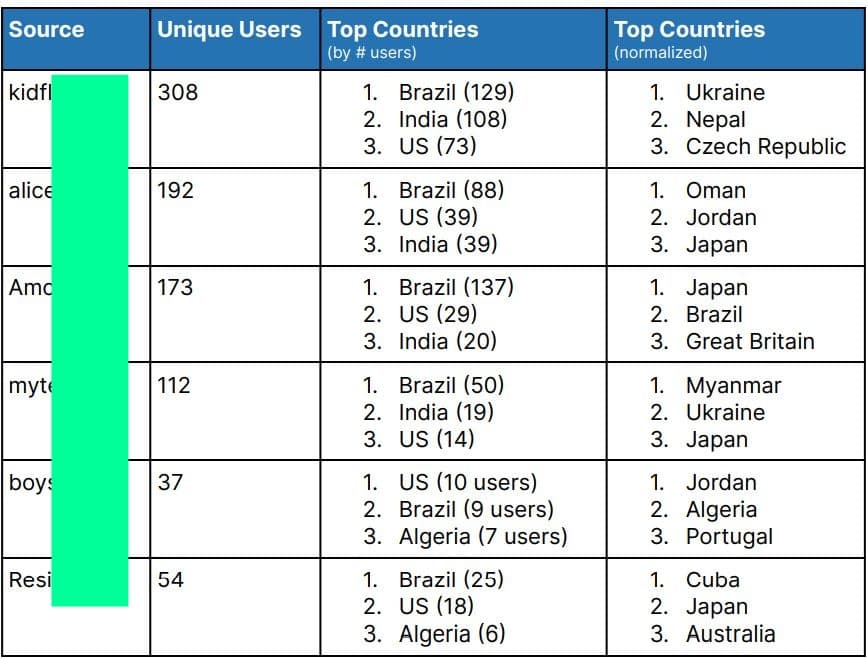
Recorded Future’s study shows infostealer logs’ potential in identifying CSAM consumers and new trends. Law enforcement agencies can use this information to track down and prosecute those who are involved in the production and distribution of CSAM.
- Hackread.com has redacted the top 10 CSAM forums to prevent users from searching for or visiting them. ↩︎
RELATED TOPICS
- INTERPOL Busts Decade-Old Child Abuse Network
- Facebook Helped FBI Capture a Notorious Child Abuser
- Authorities seize world’s biggest dark web child abuse site
- Op protected childhood: 113 online child predators arrested
- Europol Busts Major Online CSAM Racket in Western Balkans
- Utilizing Programmatic Advertising to Locate Abducted Children
[ad_2]
Source link