[ad_1]
KEY FINDINGS
- A new malware campaign targeting Azerbaijani targets has been discovered.
- The campaign uses a novel malware implant written in the Rust programming language.
- The implant is difficult to detect by security solutions and reverse engineering.
- The attackers used a decoy image file of the Azerbaijani MOD symbol in the campaign.
Organizations should take steps to protect themselves from this campaign by keeping software up to date, educating employees about cybersecurity best practices, and using a comprehensive security solution.
A new malware campaign targeting Azeri infrastructure has been discovered by the Deep Instinct Threat Lab. The campaign is notable for its use of a novel malware implant written in the Rust programming language.
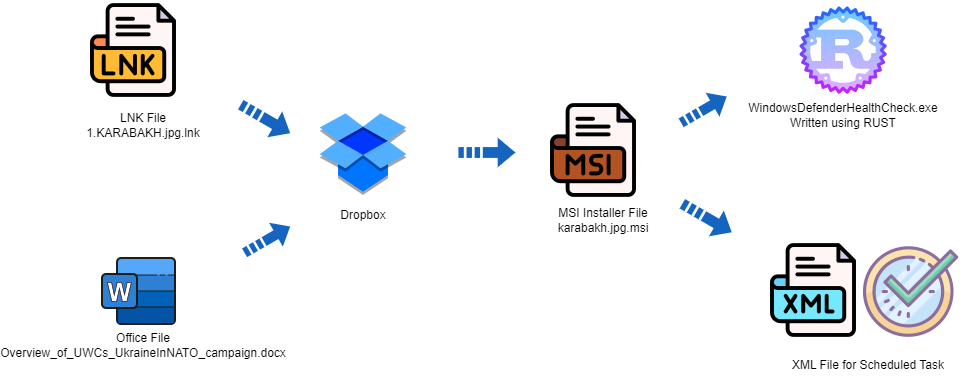
The campaign has at least two different initial access vectors. The first is a malicious LNK file with the filename “1.KARABAKH.jpg.lnk.” This file has a double extension to lure the victim into clicking on it, as it appears to be an image file related to the recent military conflict in Nagorno-Karabakh.
The LNK file downloads and executes an MSI installer hosted on Dropbox. This installer then drops an implant written in Rust, an XML file for a scheduled task to execute the implant, and a decoy image file. The image file includes watermarks of the symbol of the Azerbaijani Ministry of Defense (MOD).
The second initial access vector is a modified version of a document that was previously used by the Storm-0978 group. This document exploits CVE-2017-11882 in Microsoft Equation Editor to download and install a malicious MSI file. This MSI file also drops a variant of the same Rust implant, as well as a decoy PDF invoice.
Once the Rust implant is executed, it goes to sleep for 12 minutes. This is a known method to avoid detection by security researchers and sandboxes. The implant is then expected to gather information and send it to the attacker’s server.
According to Deep Instinct Threat Lab’s blog post, could not attribute these attacks to any known threat actor. However, the fact that both Rust implants had zero detections when first uploaded to VirusTotal shows that writing malware in esoteric languages can bypass many security solutions.
Implications of the Campaign
The use of a Rust implant in this campaign is significant for several reasons. First, Rust is a relatively new programming language, and it is not yet widely used by malware authors. This makes it more difficult for security products to detect Rust malware.
Second, Rust is a compiled language, which means that the malware is converted into machine code before it is executed. This makes it more difficult to reverse engineer the malware.
Azerbaijan and Armenia have been engaged in several conflicts, which have witnessed a significant number of cyber attacks. However, it’s essential not to overlook or dismiss recent tensions between Azerbaijan and Iran as a potential cause of this malware campaign.
Recommendations for Organizations
Organizations should take the following steps to protect themselves from this campaign and other similar attacks:
- Keep software up to date, including operating systems and security solutions.
- Be careful about clicking on links in emails and messages, even if they appear to be from known senders.
- Educate employees about cybersecurity best practices, such as phishing awareness and password security.
- Use a security solution that can detect and block malware written in esoteric languages.
Conclusion
This new malware campaign targeting Azerbaijani targets serves as a reminder that attackers are continuously developing new techniques to bypass security solutions. Organizations must take the necessary steps to safeguard themselves from these threats.
While common sense is a valuable defence against such attacks, organizations should also contemplate transitioning their infrastructure from Windows to Linux as an additional security measure.
[ad_2]
Source link