[ad_1]
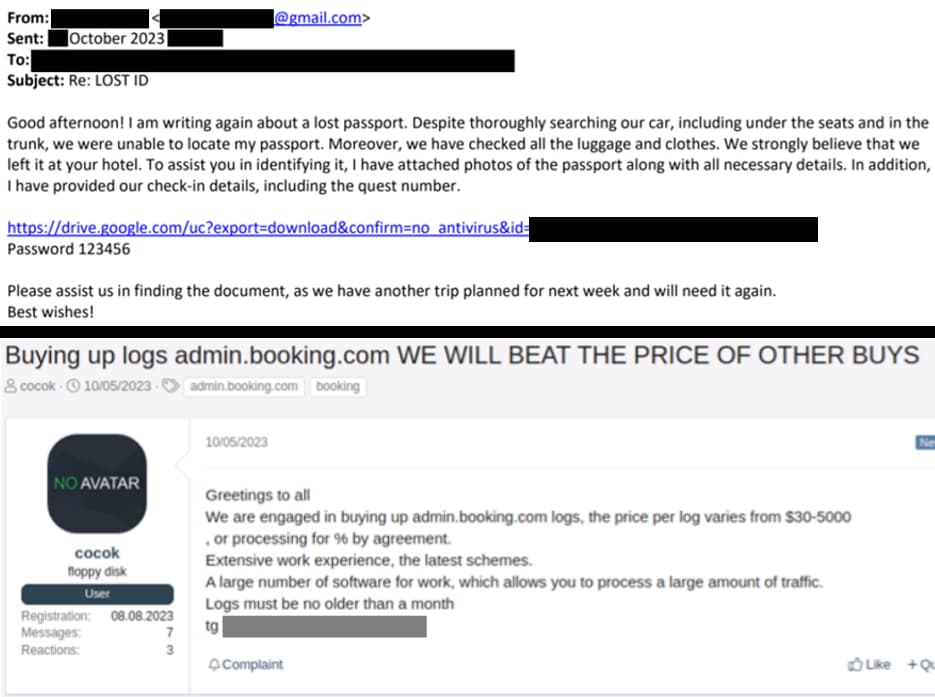
The ‘How To’ guide for targeting Booking.com customers is being offered for sale on the dark web, as well as on underground cybercrime forums, including Russian-speaking platforms such as XSS.IS.
Cybersecurity firm Secureworks is alerting Booking.com customers to a recently identified scam wherein hotels’ Booking.com accounts are compromised to deceive users into divulging their payment details.
This fraudulent activity was detected in October 2023. Researchers have observed that cybercriminals successfully obtained access to hotel login credentials through the utilization of the Vidar information stealer.
While this tool is not commonly employed in such scams, in this instance, the Vidar infostealer is utilized to infiltrate the hotel’s Booking.com portal. This unauthorized access enables cybercriminals to peruse upcoming bookings and communicate directly with guests while posing as hotel staff.
Researchers from Secureworks Counter Threat Unit™ (CTU) suspect that this may be part of a broader campaign specifically aimed at targeting Booking.com users. The purloined data is presumed to be traded on underground marketplaces or forums, where it can command a higher price due to the increased potential for defrauding unsuspecting guests.
Characterizing it as a sophisticatedly crafted scam, researchers highlight that the hackers devised an email aimed at gaining the trust of hotel employees. The deceptive message purportedly originated from a former guest who reported losing their ID or other valuables, seeking assistance from the hotel staff to locate the items.
The subtlety of this approach meant the employee did not find it suspicious, especially since the email lacked attachments or dubious links, creating the illusion of a genuine request. Consequently, the employee responded and offered assistance.
However, a link within the email, allegedly containing a photo of the lost item, actually served to install the Vidar infostealer. Once activated, this malware illicitly acquires the hotel’s Booking.com login credentials, facilitating unauthorized access to guest reservation details.
The hook in this scam creates a sense of urgency for the guests. The attacker contacts those having reservations at the hotel through Booking.com. Guests receive urgent emails from the hotel demanding immediate payment confirmation to avoid booking cancellation. This doesn’t raise any suspicions.
Rather, it panics the guests, and they click on the provided link. According to Secureworks’ report, this leads them to a fake website designed to look like Booking.com, which was created to steal their payment data.
The scammers scam the guests by draining their accounts using the stolen payment data. Moreover, they sell Booking.com credentials on the Dark Web for up to $2,000.
Although Booking.com hasn’t been directly breached, the company is cooperating with impacted hotels to improve security and help affected customers. The company emphasized using machine learning to detect suspicious activity and advised hotels and customers to stay vigilant and never provide payment details without verifying the website.
“Due to the rigorous controls and the machine learning capabilities we employ, we can detect and block the overwhelming majority of suspicious activity before it impacts our partners or customers. We have also been sharing additional tips and updates with our partners about what they can do to protect themselves and their businesses, along with the latest information on malware and phishing so that they are as up-to-date as possible on the latest trends that we’re seeing.”
“It’s good to remember that no legitimate transaction will ever require a customer to provide their credit card details by phone, email, or text message (including WhatsApp)”, Booking.com stated.
This incident highlights the evolving tactics of cybercriminals and the importance of vigilance, even for seemingly harmless requests. Hotels should be especially cautious of suspicious emails and enable multi-factor authentication on Booking.com and other platforms to add an extra layer of security.
Chris Hauk, Consumer Privacy Advocate at Pixel Privacy, shared his comments with Hackread.com, stating that this scam is designed to target hotels with good reputations.
“This scam preys on hotels that offer good customer service, making the hotel employees believe that they are aiding a customer in retrieving a lost item. This is the first time I’ve heard of scammers taking that approach. The second step in the scam involves using a customer’s Booking.com information to convince the customer that they need to make a payment immediately.”
“Organizations like Booking.com need to work with their partners to ensure that all systems and applications are kept up to date to close security holes. Also, employee training to make them aware of how scammers work is also a must” Hauk added.
RELATED ARTICLES
- The Benefits Of Blockchain In The Travel Industry
- Newly Surfaced ThirdEye Infostealer Targeting Windows Devices
- Fake ChatGPT and AI pages on Facebook are spreading infostealers
- Hotel reservation platform leaks user data from top online booking sites
- Hackers steal sensitive data from Japanese search engine for sex hotels
[ad_2]
Source link
