[ad_1]
The scam primarily targets popular Russian online marketplaces like YULA or OLX, but ESET researchers also observed non-Russian targets, including eBay, Sbazar, Jófogás, and BlaBlaCar.
In their latest report, ESET researchers have disclosed their findings on the Telekopye toolkit that simplifies online scamming for individuals with limited technical expertise. This is a follow-up report. The company shared a preliminary analysis on Telekopye in August 2023.
Researchers have delved deeper into the onboard process of the scammers to unearth the wicked scamming operation, including the explanation of different scam scenarios they are using to deceive users.
About Telekopye Toolkit
Telekopye Toolkit is implemented as a Telegram bot and helps cyber criminals scam unsuspecting users in online marketplaces. This tool allows scammers to create phishing websites, fabricate fake screenshots, and transmit emails, SMS messages, etc.
As per ESET telemetry, Telekopye Toolkit is operational and under active development. The scammers call their victims Mammoths, and ESET has assigned scammers the name Neanderthals.
How Are Scammers Recruited?
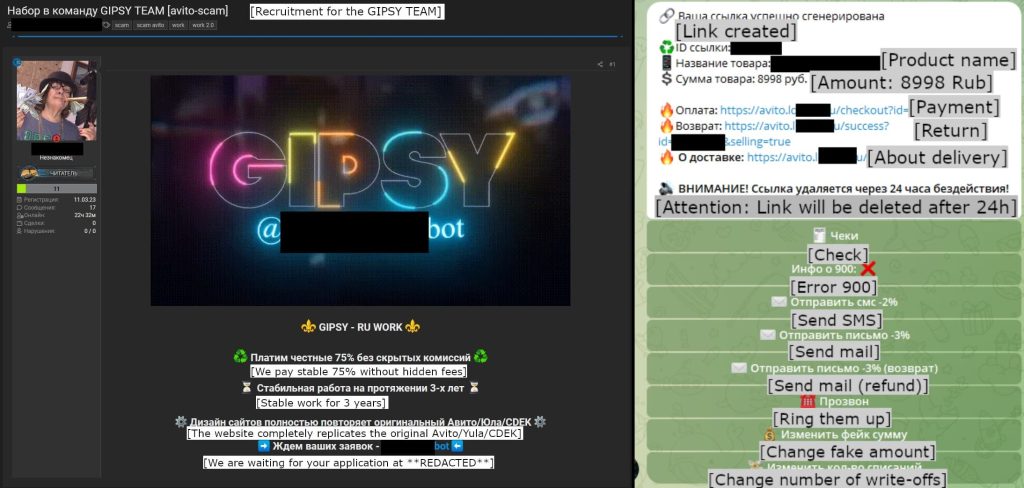
Research reveals that scammers (ESET researchers have named the scammers utilizing Telekopye Toolkit as Neanderthals) are recruited via advertisements distributed across different online channels, mainly underground forums. These ads are designed to defraud online marketplace users.
Interested Neanderthals have to complete an application form and answer key questions about their previous experience in this kind of work. Existing group members approve them with relevant ranks and give them full access to Telekopye’s functionalities.
Scam Scenarios:
In a blog post, ESET researchers identified three different scam scenarios.
1. Seller Scam
In this scam, attackers pose as sellers and entice users into purchasing items that don’t exist. Suppose the victim expresses interest in buying the item. In that case, the seller lures them into making an online payment and gives them a phishing website link, which appears as a legitimate payment portal. But this website solicits the victim’s banking credentials or credit card details (may even provide balance information) and transfers the data to the scammers. Sellers internally refer to this scam as 1.0.
2. Buyer Scam
This scam is referred to as 2.0. Attackers pose as buyers in this scam and target their victims after comprehensive research. They express interest in an item and claim to have paid through the provided platform. They send the victim a Telekopye Toolkit-created SMS or email containing a link to a phishing website. The victim is persuaded to click this link to receive the payment from the platform. The remaining method is similar to the seller scam.
3. Refund
This scenario entails Neanderthals creating a situation where the Mammoth expects a refund. The scammer sends them a phishing email with a link to a phishing website. This email can be sent to victims the scammers haven’t contacted before or used in combination with the seller scam. They exploit the greed of victims who want this non-existent refund. In seller scams, when the victims don’t receive the goods, they are again scammed by Neanderthals via refund phishing emails.
Every Neanderthal had to join a group where they communicated the rules and manuals and another channel where transaction logs were stored. Telekopye Toolkit attackers refer to law enforcement and researchers as rats and try to stick to their rules.
The scam primarily targets popular Russian online marketplaces like YULA or OLX, but ESET researchers also observed non-Russian targets, including eBay, Sbazar, Jófogás, and BlaBlaCar.
If you are a Telegram user, there are several ways to protect yourself from such bots including the following:
- Be wary of unexpected messages and links. If you receive a message from someone you don’t know, or if you receive a link that seems suspicious, don’t click on it. Instead, report the message or link to Telegram.
- Never give out your personal information to a Telegram bot. This includes your name, address, phone number, email address, and password.
- Be careful about what you download from Telegram bots. Only download files from bots that you trust.
- Keep your Telegram app up to date. Telegram releases security updates regularly, so make sure you have the latest version installed.
- Report any suspicious activity to Telegram. If you think you may have been scammed by a Telegram bot, report it to Telegram immediately.
RELATED ARTICLES
- RIG Exploit Toolkit Distributing CeidPageLock Malware
- Telegram and Discord Bots Delivering Infostealing Malware
- New credit card skimmers channel funds through Telegram
- New Phishing Attack Spoofs Microsoft 365 Authentication System
- Chinese APT Slid Fake Signal and Telegram Apps onto Official App Stores
[ad_2]
Source link