[ad_1]
The exploited WinRAR vulnerability was a zero-day flaw identified in August 2023 – Despite subsequent patching efforts, unpatched systems remain at risk and continue to be targeted.
Cybersecurity researchers at Deep Instinct Lab have revealed a new series of cyberattacks carried out by ‘UAC-0099,’ specifically targeting Ukrainians. These attacks employ common tactics such as using fabricated court summons to entice targets into executing malicious files.
The group’s activities were initially revealed in May 2023 through the Ukrainian CERT advisory ‘#6710,’ and Deep Instinct has now provided exclusive insights into their latest attack.
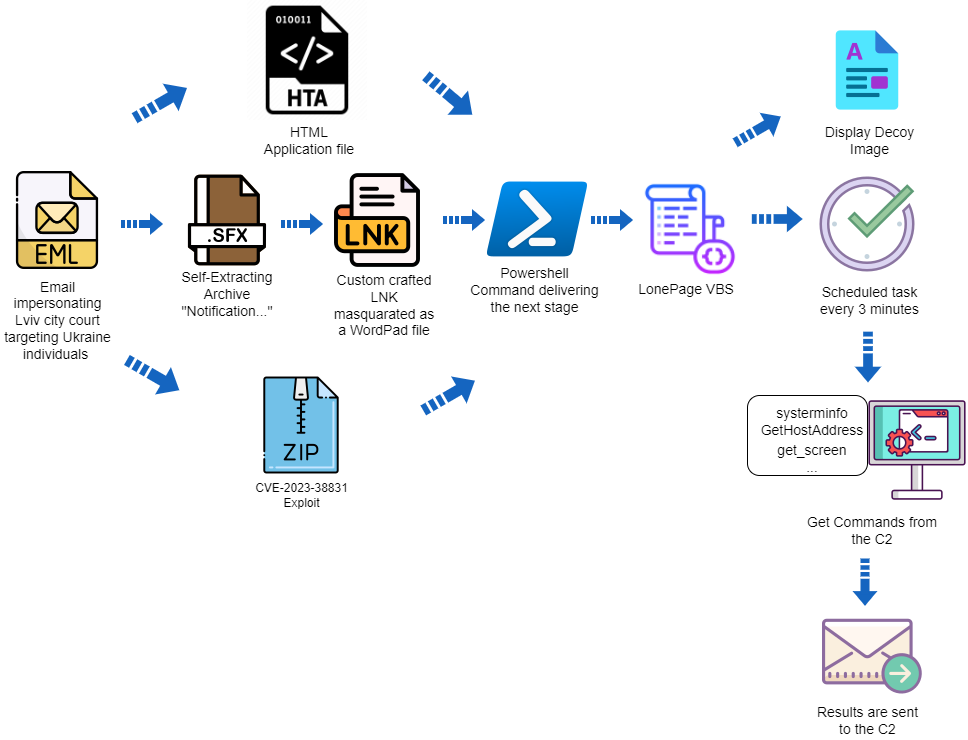
According to a blog post from the company, on December 21st, 2023, ‘UAC-0099’ utilized an email scam to impersonate the Lviv city court via the ukr.net email service. The target was a Ukrainian employee working remotely for a company outside Ukraine. The deceptive email contained an executable file created by WinRAR, named docx.lnk.
Although appearing as a regular document, it was an LNK shortcut designed to execute PowerShell with malicious content, decoding two base64 blobs and writing the output into VBS and DOCX files.
The VBS malware, identified as ‘LonePage’ by CERT-UA, establishes a concealed PowerShell process that communicates with a predefined C2 URL to retrieve a text file. The script verifies the presence of the string ‘get-content’ in the text file, subsequently executing the code from the server and saving it as an array of bytes.
The LonePage VBS (VBS) proves to be a potent tool, enabling cybercriminals to infiltrate computers and execute malicious code. Employing a deceptive tactic, it utilizes a DOCX decoy document, tricking victims into believing they are opening a legitimate file. Employing a method akin to the LNK attack vector, the HTA technique involves an HTML file incorporating a VBScript that executes PowerShell with a recurring four-minute task cadence.
In both incidents, the pro-Russian gang exploited a recognized WinRAR vulnerability, designated as CVE-2023-38831 in August 2023, and identified by Group-IB. This vulnerability arises from the way WinRAR processes ZIP files, requiring user interaction with a specially crafted ZIP archive for exploitation.
The attacker crafts a seemingly harmless archive by appending a space after the file extension. This archive contains a folder with an identical name and an extra file bearing a “.cmd” extension.
When a user double-clicks on the innocuous file, the associated “cmd” file is executed instead. This vulnerability heightens the risk of widespread infections, as even security-aware victims may inadvertently run malicious code while opening what appears to be a harmless file.
Researchers have found this gang’s tactics simple yet effective. They rely on PowerShell and create a scheduled task to execute a VBS file. Monitoring/restricting these components can reduce the risk of “UAC-0099” attacks and help identify them quickly in case of compromise.
This isn’t the first time Russian hackers have exploited known vulnerabilities. In early December, Hackread.com reported how the Russian GRU’s affiliated Forest Blizzard exploited an Outlook vulnerability allowing attackers to steal Net-NTLMv2 hashes and access user accounts.
On December 15, 2023, reports surfaced that Russian hackers breached a major US biomedical company in a TeamCity-linked attack. Despite the vulnerability, which scored 9.8 on the CVSS scale, being patched in September 2023, unpatched systems remain susceptible to ongoing cyberattacks.
RELATED ARTICLES
- Russian Midnight Blizzard Hackers Hit MS Teams in Precision Attack
- Russian Hackers Employ Telekopye Toolkit in Broad Phishing Attacks
- Microsoft warns of rising NOBELIUM credential attacks on defence sector
- Microsoft Outlook Vulnerability Exploited by Russian Forest Blizzard Group
- Russia Hackers Abusing BRc4 Red Team Penetration Tool in Recent Attacks
[ad_2]
Source link