[ad_1]
According to cybersecurity researchers at Halcyon AI, the new Volcano Demon ransomware gang calls its victims “very frequently, almost daily in some cases.”
A new and particularly menacing ransomware group known as “Volcano Demon“ has surfaced, causing alarm across manufacturing and logistics industries. This group has deviated from the usual ransomware playbook, opting for a more direct and intimidating method to coerce their victims.
Over the past two weeks, “Volcano Demon“ has successfully targeted several companies, deploying their unique ransomware called “LukaLocker” in at least 2 cases. This malicious software encrypts files with the .nba extension and is designed to evade detection and analysis, making it a formidable threat.
According to cybersecurity firm Halcyon, What makes “Volcano Demon“ stand out is their use of phone calls to pressure company executives into paying ransoms. Instead of the typical data leak sites, they rely on frequent, threatening calls from unidentified numbers. Tim West, an analyst at Halcyon, shed light on this unsettling tactic. “They call very frequently, almost daily in some cases,” he said.
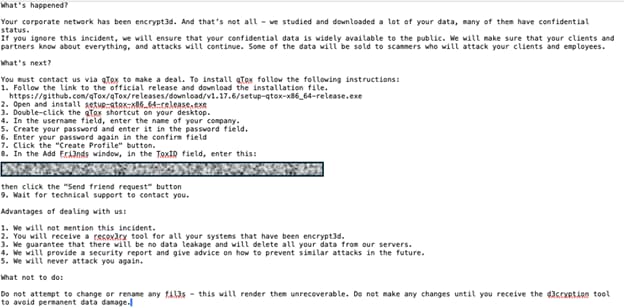
Before launching their ransomware attacks, Volcano Demon infiltrates sensitive data to command-and-control (C2) servers. This stolen data is used as leverage to pressure victims into complying with their demands. The ransom note left by the attackers is blunt and threatening: “If you ignore this incident, we will ensure that your confidential data is widely available to the public.”
Tracking down Volcano Demon has proven to be a significant challenge for cybersecurity experts. The group clears log files on the compromised machines before executing their attacks, making it nearly impossible to conduct thorough forensic evaluations. This approach has made it difficult to trace their origins and understand the full scope of their operations.
As explained by Adam Pilton, a senior cybersecurity consultant at CyberSmart, the element of calling complicates the extortion process due to the unpredictability of the unknown caller ID as well as the calling instances. Requiring a negotiator to be ready at all times would result in these incidents being even more costly for the victim company. However, there could also be new leads for law enforcement to follow, Pilton added.
“Traditionally, IP addresses are very simple to hide behind and although telephone data can be obscured, the information the attacker gives away is potentially so much more,” he said. “Here will be voice data and potential background noise, as well as the call connection records.”
RELATED TOPICS
[ad_2]
Source link