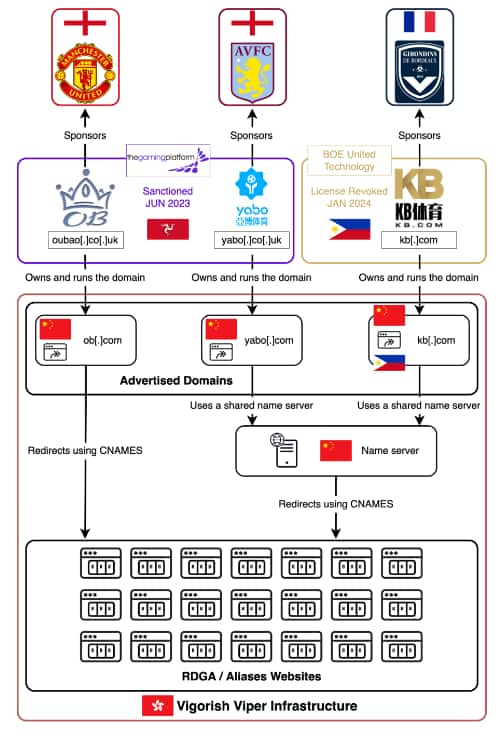
The Identity Theft Resource Center® (ITRC), a nationally recognized nonprofit organization established to support identity crime victims, released its U.S. data breach findings for the second quarter (Q2) and the first half (H1) of 2024.
The results are staggering, revealing a dramatic increase in data breach victims, with a 490 percent rise compared to the first half of 2023.
This alarming trend underscores the urgent need for enhanced data and identity protection measures across all sectors.
According to the ITRC, there were 732 publicly reported data compromises in Q2 2024. While this represents a 12 percent decrease from the previous quarter (838), the overall picture for the year’s first half is far more concerning.
The ITRC tracked 1,571 compromises in H1 2024, marking a 14 percent increase compared to H1 2023, which ended with a record number of compromises (3,203).
Explosive Growth in Victim Numbers
The number of data breach victims in H1 2024 reached an unexpected 1,078,989,742, a 490 percent increase from the 182,645,409 victims reported in the first half of 2023.
Many of these victims were impacted by breaches announced or updated in Q2. For instance, Q1 saw 37,677,141 victims, while Q2 witnessed a staggering 1,041,312,601 victims. Several high-profile breaches contributed to these alarming numbers.
Prudential Financial initially reported a breach in February 2024, affecting 36,000 victims. However, in June 2024, this figure was revised to 2.5 million.
Protect Your Business Emails From Spoofing, Phishing & BEC with AI-Powered Security | Free Demo
Similarly, Infosys McCamish System revised its victim count from approximately 84,000 in February to 6 million.
Credential stuffing attacks targeting the Snowflake cloud service customers accounted for over 900 million victims reported in Q2.
The estimated number of H1 victims is 1+ billion, not including those affected by the Change Healthcare supply chain attack.
Company executives predict this breach will impact “a substantial number” of U.S. residents, further deepening the alarming situation.
Expert Insights
Eva Velasquez, President and CEO of the Identity Theft Resource Center, emphasized the gravity of the situation.
The H1 2024 Data Breach Analysis findings are eye-opening for many reasons. The estimated victim count is up significantly, primarily due to a small number of substantial data events skewing the numbers.
What is clear, though, is the fact the trends we saw emerge in 2023 that led to a record-breaking year in compromises are continuing into 2024.
Velasquez added that the trends accelerated through the year’s first half in some cases, such as the number of organizations impacted by supply chain attacks and the number of entities that did not list the root cause of a breach.
The takeaway from this report is simple: Every person, business, institution, and government agency must view data and identity protection with a greater sense of urgency.
Key Findings
The H1 2024 Data Breach Report & Analysis revealed several critical trends:
- Unspecified Causes: “Not Specified” remained the most reported cause of a cyberattack listed in breach notices issued in H1 2024, accounting for 68 percent of cases.
- Industry-Specific Attacks: Attacks against Financial Services companies surged by 67 percent year-over-year, making it the most compromised industry in H1 2024, followed by Healthcare companies. Reported compromises increased in ten of the 16 industries tracked by the ITRC. However, Healthcare entities saw a 37 percent year-over-year decrease in reported compromises, dropping from the most targeted industry to the second most frequently compromised for the first time in six years.
- Driver’s License Data Theft: The increased value and use of stolen Driver’s License information were evident. Driver’s License data was stolen in 25 percent of data breaches based on notices issued in H1 2024. This trend reflects a post-pandemic shift towards using Driver’s Licenses for identity verification on a broader variety of transactions. Data breaches involving Driver’s License data rose from 198 instances in pre-pandemic 2019 to 636 in 2023 and 308 through June 30, 2024.
The ICRC’s H1 2024 Data Breach Report & Analysis highlights the urgent need for robust data protection measures.
As data breaches continue to rise, affecting millions of individuals and numerous industries, safeguarding personal information cannot be overstated.
The ITRC remains committed to providing support and guidance to victims of identity crime and advocating for stronger data security practices.
Join our free webinar to learn about combating slow DDoS attacks, a major threat today.