Sam Bright, VP & GM of Google Play, briefing the media on the new Google Play features | Photo Credit — Stephen Bondio for Google
Enhanced discovery and personalized recommendations
Google Play is going all in on AI and is leveraging it to simplify app discovery. As such, Google Play will now include AI-generated app reviews and FAQs which offer concise summaries of user feedback and frequently asked questions. Additionally, a new AI-powered feature helps users compare apps in similar categories, streamlining decision-making.
Google Play’s multi-select interest filters | Image credit — Google
Personalized recommendations are a key focus. To address this, Google has introduced multi-select interest filters allows users to manually specify their preferences, ensuring more relevant game suggestions based on individual gaming interests.
Curated spaces and comics in Japan
Curated spaces in Google Play cater to specific interests, offering a centralized hub for content exploration. Following a pilot for cricket enthusiasts in India, Google Play has partnered with Japanese comic publishers to launch a dedicated space for comics in Japan. Users can access comics-related content, including free previews, events, trailers, and reviews, all in one place.
Sample of “Chainsaw Man” manga in Google Play | Image credit — Google
Unfortunately, this experience is currently only available in Japan and in Japanese. During the briefing, the question came up several times on whether this would eventually expand to other regions. However, Google had no further information to share on that at this time. Hopefully, this is something that can be made possible in the future.Enhanced gaming experience
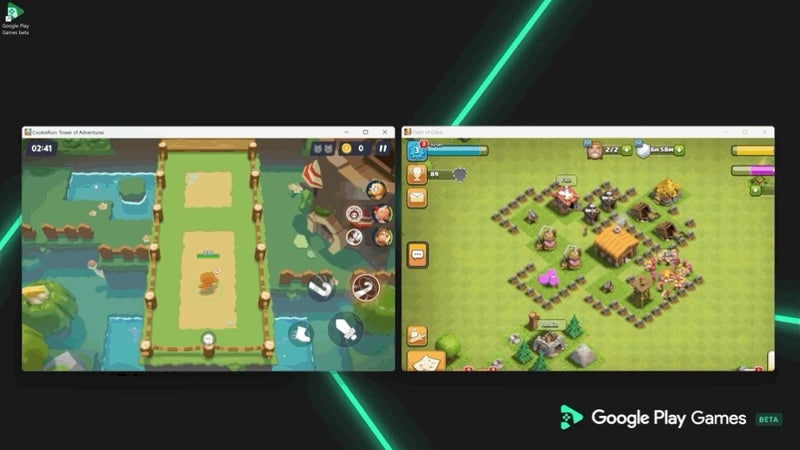
Play Pass, Google’s subscription service, provides access to over 1,000 games and apps without ads or in-app purchases. However, Play Pass will now expand its offerings by including new deals in Asphalt Legends Unite, Call of Duty: Mobile, Candy Crush Saga, and the upcoming addition of Kingdom Rush 5: Alliance. New subscribers in select regions will be able to enjoy a significant discount for their first three months.However, the highlight of the changes across gaming is the expansion of Google Play Games on PC, which will now allow users to enjoy mobile games on multiple devices seamlessly.
Multiscreen and multi-game experience on Google Play Games | Images credit — Google
These changes will allow you to start a game on your mobile device, and then seamlessly switch it over to your PC if you wanted. The upcoming multi-game capabilities will enable PC gamers to play multiple titles simultaneously, enhancing the overall gaming experience.
Rewarding loyalty
Google Play Points, one of the world’s largest rewards programs, is stepping up its offerings. Super Weekly Prizes will give Diamond, Platinum, and Gold members a chance to win enticing prizes like Pixel devices, Razer gaming products, and merchandise. The program also offers exclusive experiences, such as a recent Pokémon GO Fest event and an upcoming Marvel Games event at San Diego Comic-Con.Google Play super weekly prizes can get you some very nice new tech | Images credit — PhoneArena
Personalized content and privacy controls
The new Collections experience in the U.S. will curate relevant content from various apps directly on the home screen. Automatically organized categories like Shop, Watch, and Listen simplify content discovery and resumption.Google Play’s personalized content into categories | Images credit — Google
Google Play prioritizes transparency and control, so users can now manage their app data preferences through “Personalization in Play,” ensuring a tailored experience while respecting privacy choices.With these new features and enhancements, Google Play is striving to become a more engaging and personalized platform, helping users discover, enjoy, and get rewarded for their favorite apps, games, and content.
[ad_2]
Source link