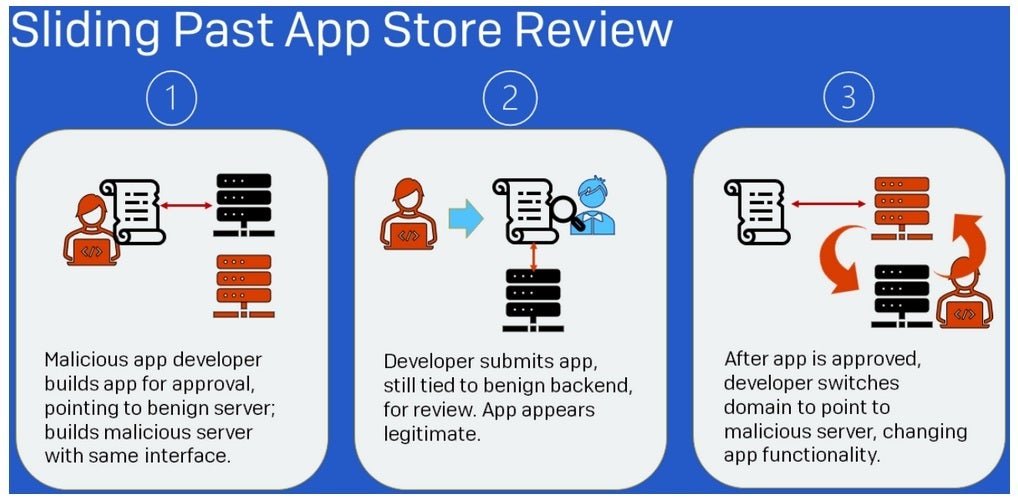
We take a look at what the Android 14 developer preview means for Android security moving forward.
Android developers have been given a taste of what’s to come in the next big step up in mobile land, thanks to Android 14 waiting on the horizon. The developer preview is a great way for those most familiar with the mobile operating system to see which changes they’ll enjoy and what ones they’ll have to endure.
As it happens, there’s quite a few security changes coming down the pipeline and developers will now be busy testing their apps. Not only are alarm permissions, system broadcasts, and language support experiencing alterations, but a wealth of security features will help ensure your device is as safe as can be.
Out with the old, in with the new
The biggest change is that old apps are on the way out. After a certain point, you will no longer be able to install them. These kinds of changes have been threatening to land for some time now, so developers will surely have been aware of this coming.
As Ars Technica notes, the current backward compatibility system allowed for older apps to still install but at the risk of malware developers simply targeting older Android versions.
Android 14, on the other hand, is simply bringing down the curtain and those old apps won’t install anymore. Now, don’t panic too much. Your favourite apps are almost certainly safe, especially if you’re still using them on a daily basis because there’s a strong chance they’re still being maintained and updated.
By “old apps”, we’re talking Android 6 and earlier which is a grand total of 8 years+. Given that apps not updated for two years have already started to be hidden from view on the Play store, there is a tiny chance you’ll be impacted by this. If you’re a side-loading hobbyist with a passion for ancient apps, then maybe this could cause you a few headaches. For most people, this is one of those changes you simply won’t notice. It’s a smart piece of house cleaning by Google and one which makes sense.
The first of what could be many security changes
Additional security features and alterations mentioned on the Android Developers Google blog are as follows:
Safer dynamic code loading
Dynamic code loading (DCL) introduces outlets for malware and exploits, since dynamically downloaded executables can be unexpectedly manipulated, causing code injection. Apps targeting Android 14 require dynamically loaded files to be marked as read-only.
Malware authors being hampered from malicious code injection can only be a good thing so this is good to see.
Runtime receivers
Apps targeting Android 14 must indicate if dynamic Context.registerReceiver() usage should be treated as “exported” or “unexported”, a continuation of the manifest-level work from previous releases.
Safer implicit intents
To prevent malicious apps from intercepting intents, apps targeting Android 14 are restricted from sending intents internally that don’t specify a package.
Both of the above have the intent of locking down data from other apps or the system itself. As Bleeping Computer points out, rogue apps and other malicious activities on an Android will have a much more difficult time if trying to intercept pieces of information intended for somewhere else.
A full rundown of what’s to expect (so far) can be seen on the official site. It’s worth noting that a complete reveal of what Android 14 will contain is not likely to be seen for some time yet, so all of this is subject to change to some degree.
Keeping your phone safe
This is all good news for the future, but what can you do in the here and now to keep harm at arm’s length?
- Update your apps, and your device. Keep your Android device up to date, and allow your apps to update automatically. Depending on your version, you should be able to tell your device to update when connected to your Wi-Fi as opposed to taking a bite out of your roaming data.
- Enable your lock screen. Whether you’re using a pattern, a PIN, a password, or even your thumbprint, it should be at the top of your list. Pay attention to how long your phone is unlocked before it reverts to the lock screen. This is a valuable window for criminals should you leave your phone unattended.
- Enable the “find my phone” service. This, combined with the lock screen, will help keep your data safe in cases where you need to delete all data from the device remotely.
- Install security tools on your phone. This will help provide you with maximum protection from rogue links, bad apps, and more.
- Only download from official stores. Bad things do end up on there, but it’s still safer than allowing installations from unknown sources via third party websites.
- Always read the reviews. You’ll not only gain insight into what the app is doing, but you’ll also make sure that the apps you’re using are still supported. This will keep you away from potentially exploitable software which has long since fallen into disrepair. Remember: there’s a two year expiry on abandoned apps before they’re removed from the Play store, so not everything put out to pasture will vanish right away.
Stay safe out there!
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.
[ad_2]
Source link